
Secure Your dmarcian Account with Two-Factor Authentication
dmarcian is happy to announce Two Factor Authentication for user accounts. The new security feature allows token based authentication with an app, such as Authy or Google Authenticator, or FIDO Universal Second Factor (U2F) which enables physical security keys like Yubikey or Nitrokey. You can read Google’s recent research paper, “Security Keys: Practical Cryptographic Second Factors for the Modern Web,” to learn about the benefits realized in using U2F-based two-factor authentication.
Setup Instructions
If you would like to setup 2FA, log into your account and visit the account preferences page. Then scroll down to the Two Factor Authentication section.
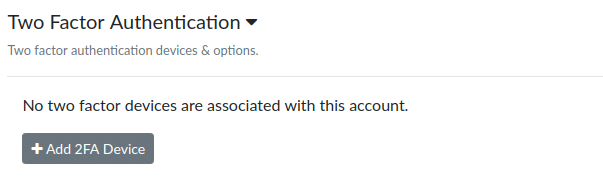
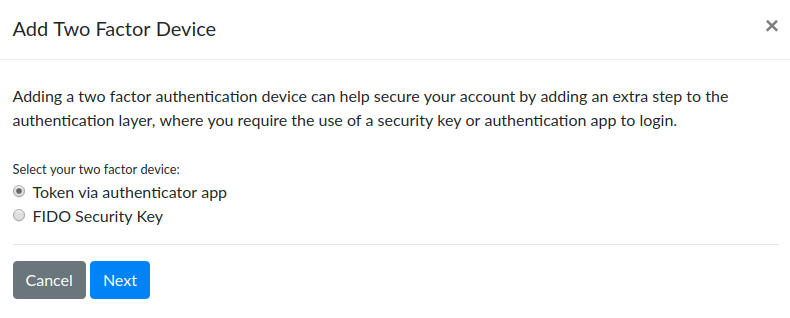
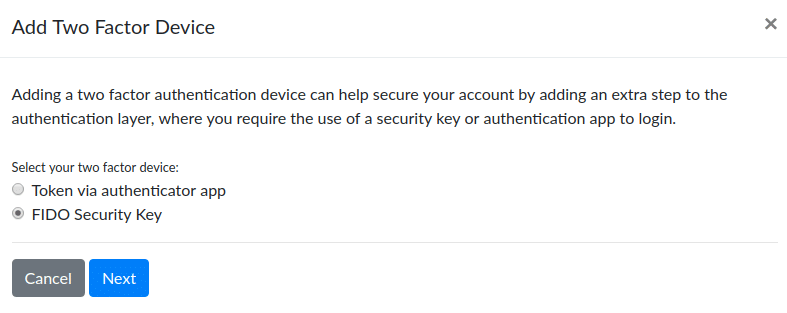
Click “Add 2FA Device” and you will see a dialog that asks which type of device you would like to add.
Token via Authenticator App
Token based authentication works by presenting you with a QR code that you can scan with an app. Once scanned, that app will produce a code every few minutes that you will enter when prompted during your login. Token based authentication is generally associated with mobile applications but there are also some desktop applications.
There are number of choices for both iOS and Android devices (including watches), and we have linked a few of the most popular options.
There are also options on the desktop, either as a standalone app or a browser extension.
- Authy – MacOS, Windows (app) and Linux (browser extension)
- Yubico Authenticator – MacOS, Windows and Linux (app)
- 1Password – MacOS, Windows (app) and Linux (browser extension)
- Bitwarden – MacOS, Windows and Linux (app & extension)
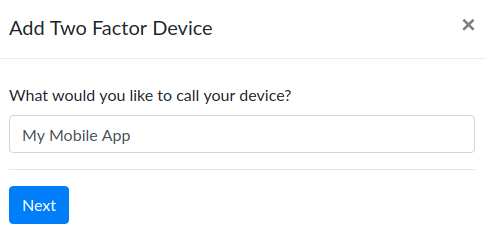
Once you have an authenticator application setup, choose Token via Authenticator App and click Next. You will see a prompt to name your device because you can setup multiple token authentication apps or devices. Give this one a name to help you identify it and click next.
Next you’ll be presented with a dialog box that shows a QR code image and a confirmation box. Open your authenticator app and use it to scan the QR code. On a mobile device, the app will access your camera while a desktop application will need to highlight a section of the screen. Below is an example only, you will see your own unique code.
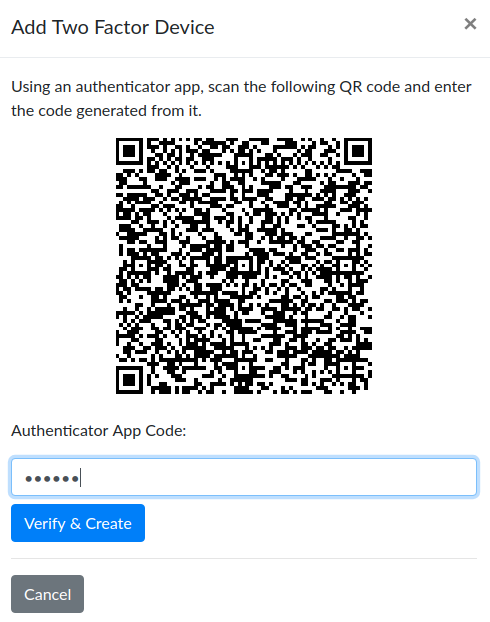
Once you have scanned the image, your app should show you a 6-digit code. Type that code into the Authenticator App Code box and click Verify & Create. Remember, the code will change every minute or two so if it doesn’t work the first time, you may need to use a new code. Most authenticator apps have an indicator that shows how long the code will work.
After the app has been verified, you are all set to use the application but there’s one last safety step. Phones get lost or misplaced and you don’t want to be locked out of your account if that happens, so we provide you with ten backup codes that can each be used once. Store these in a safe place, like a password manager application or even printed in a locked file. You won’t use these unless you have lost your device. You can either copy them or download them.
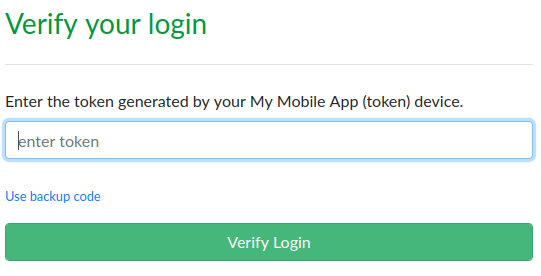
Next time you login, you will be presented with the Verify Your Login screen. Open up your app and type the code on the screen to complete the login. You can also click “Use backup code” if needed.
FIDO Universal Second Factor (U2F) Security Key
FIDO2 U2F is an open standard for using physical security keys to access online services, requiring no drivers or software to be installed on the computer. It is an approach to 2FA that creates both a better user experience and extreme security at the same time. That is a rare accomplishment. Simply log in and then tap the key when prompted.
In 2017, Google required all 85,000+ employees to use Security Keys and credits the change with completely eliminating successful phishing attacks against its employees. Here at dmarcian, we have the same employee policy and we’re excited to make the functionality available for our customers. We have tested with both Yubikeys and Nitrokey FIDO U2F, but any U2F compatible key or device should work.
FIDO U2F is supported by Google Chrome, Mozilla Firefox, Microsoft Edge, Opera and Apple Safari using WebAuthn technology. Both Google Chrome and Mozilla Firefox have supported the technology since early 2018, but if you are currently using an older browser it may not be available. Your browser will present you with an indicator to let you know if it isn’t compatible.
In order to set it up, select FIDO Security Key and click Next.
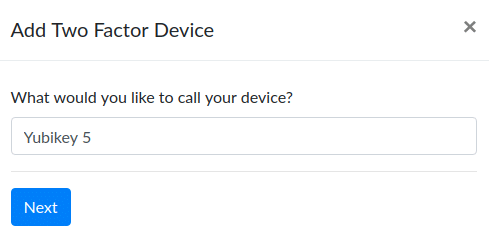
Then name your device. Since you can associate multiple 2FA devices with your account, give each one a distinctive name.
Click Next and your browser should create a dialogue prompting you to touch your security key. Once complete, the dialog will go away and you will see a verification message.
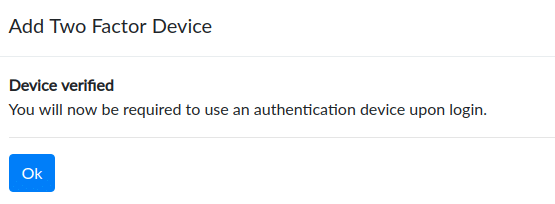
After the key has been verified, you are ready to use the application.
But there’s one last safety step. In case the key is lost or misplaced you don’t want to be locked out of your account so we provide you with ten backup codes that can each be used once. Store these in a safe place. You won’t use these unless you have lost your Security Key. You can either copy them or download them.
Next time you log in, the browser will prompt you with the same request to tap your Security Key to complete the login. If you have multiple keys, any of them will work.
Want to continue the conversation? Head over to the dmarcian Forum.



