
DK Hostmaster Workshop & Identifier Alignment
At a recent DK Hostmaster workshop, guest instructor Tim Draegen, founder of dmarcian and one of the primary authors of DMARC, helped attendees better understand how DMARC makes use of authentication to improve email security using the well-known SPF and DKIM mechanisms, how DMARC’s reporting protocols help protect your email domains quickly and precisely, and how to install DMARC in your organization.
To understand how DMARC makes use of authentication to improve email security, it is helpful to have an understanding of SPF and DKIM and how they contribute to Identifier Alignment.
SPF
SPF is a way for Internet Service Providers to verify that a mail server (IP address) is authorized to send email for a specific domain.
To use SPF, the administrator of an email domain publishes a list of servers or IP addresses that are allowed to send email on behalf of the domain. When a sender tries to hand-off email to an email “receiving” server for delivery, the email server checks to see if the sender is on domain’s list of allowed senders. If so, then a link has been established between the piece of email and the email domain.
DKIM
DKIM is a free technology that is used to link a piece of email back to a domain. When an email is sent, it is signed using a private domain key and then validated on the receiving mail server (or ISP) using a public key that is located within the DNS. This action authenticates that the content of the email was not modified during its transfer. It prevents someone from intercepting your email, altering it, then sending it along with altered information.
Identifier Alignment
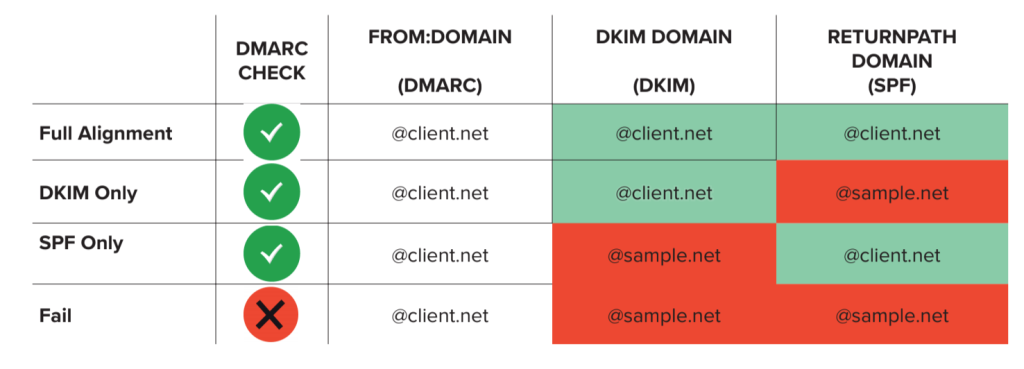
By themselves, SPF and DKIM can associate a piece of email with a domain. DMARC attempts to tie the results of SPF and DKIM to the content of email: specifically to domain found in the From:header of an email. The domain found in the From: header of a piece of email is the entity that ties together all DMARC processing.
Because anyone can buy a domain and put SPF and DKIM into place (including criminals), the results of processing SPF and DKIM have to be related to the domain found in the From:header to be relevant to DMARC. This concept is referred to as “Identifier Alignment.” Getting identifiers to align ends up being a large part of the work of deploying DMARC.
If a criminal is trying to spoof bank.com and sets up a domain criminal.net to get SPF and DKIM in place, just because SPF and DKIM both pass doesn’t mean the authentication has anything to do with bank.com.
To tie it all together, for a piece of email to be considered DMARC compliant, the domain found in an email’s From:header must match either the SPF-validated domain or the originating domain found in a valid DKIM signature. If the domains match, receivers can safely assert that the email did come from the domain from which it purports to originate. This is how easy-to-identify email is made possible via DMARC.
With a team of email security experts and a mission of making email and the internet more trustworthy through domain security, dmarcian is here to help assess an organization’s domain catalog and implement and manage DMARC for the long haul.
You can get in touch with us or register for a free trial where our onboarding and support team will help you along the way.


