
DMARC Adoption among Asia-Pacific Retailers
Consistent with global trends, phishing attacks in the Asia-Pacific (APAC) region are relentless and have grown exponentially since the pandemic. With this in mind, we’re taking a look at DMARC adoption in the retail sector by laying out adoption statistics for the top 500 APAC retail domains, along with the top 100 retail domains in New Zealand and Australia—all based on estimated revenue.
As we discussed in our previous installment of DMARC adoption research, retailers are not sheltered from cyber attacks; quite contrary, they are common targets for criminals.

The Australian Signals Directorate reports in its 2023-24 Annual Cyber Threat Report that “Most scams relate to cyber-enabled crimes, such as phishing. Phishing represents 55% of all losses and 74% of all reports. Together, there were just over 150,000 reports with over $33 million in losses.”
Because organizations continue to suffer financial losses, brand damage and loss of trust from phishing attacks, big players in the email ecosystem are beginning to self-regulate. In February 2024, Google and Yahoo began enforcing a DMARC requirement for bulk senders that was announced in October 2023 and has fueled a DMARC adoption rush for bulk senders.
Learn how DMARC can help your organization meet the PCI DSS requirements.
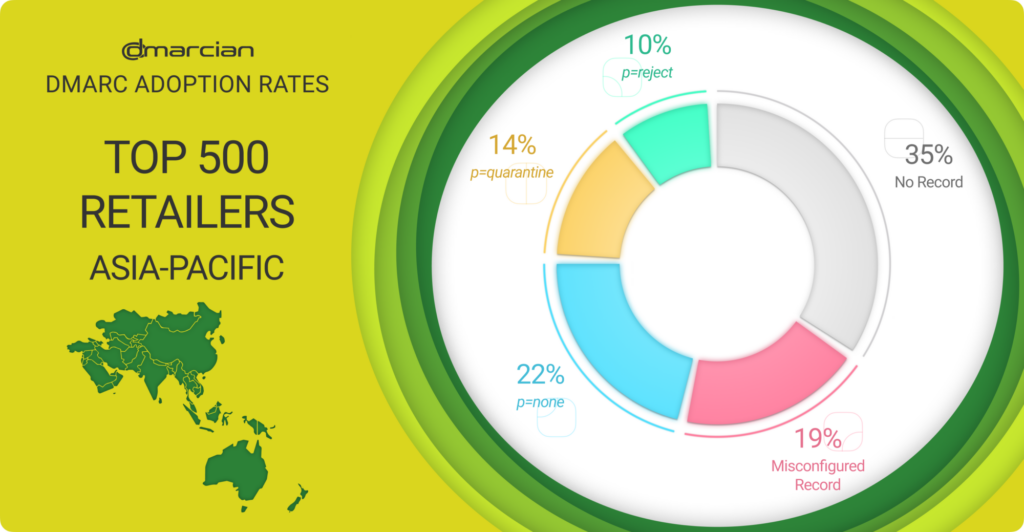
DMARC Status of the Top 500 Asian-Pacific Retailers
Our domain research reveals that 46% of the top 500 APAC domains have published a DMARC record that aligns with best practices—the first step in protecting domains from exploits.
Twenty-four percent have advanced their DMARC policies to enforcement levels of p=quarantine or p=reject. Finally, 76% of the APAC retail domains we surveyed are prone to phishing and social engineering intrusions because they have no record; issues with their record; or a p=none policy, the DMARC monitoring phase that turns on the lights so you can see who is sending email from your domains but provides no protection.
Retailers are highly reliant on email marketing. We often see mentions of “reputation” in relation to spam scores but not in the context of your “brand” reputation. Phishing impacts your reputation from a spam perspective; however, just as importantly, it can impact your reputation to the general public. Can emails from your organisation be trusted?
Tass Kalfoglou, Director of dmarcian APAC Business Unit
Lack of RUA reporting address
We discovered that 19% of APAC’s top 500 retail domains had errors or didn’t align with email security industry standards. The majority, 12%, of these problems were the lack of an RUA reporting address, which determines the email address for sending DMARC reports. Including an RUA address is a best practice; without one, there’s no way to keep in touch with your email security strategy.
The RUA, or aggregate, reports offer a view of a domain’s traffic, including the authentication status for SPF, DKIM, and DMARC. Email reporters issue RUA and RUF reports in XML format, which isn’t human friendly. Without a RUA address in the DMARC record, the domain owner is not taking advantage of one of DMARC’s core functionalities: visibility over how a domain is being used and they are effectively flying blind.
When you point your RUA address to our platform, it processes raw DMARC reports and transforms them into an easy-to-read dashboard that displays your domain’s status.
The significant number of domains with no RUA address may point to a trend of retailers implementing the bare minimum DMARC record for the sake of satisfying the email authentication requirements set by Google and Yahoo earlier in the year.
A DMARC record with a p=none security policy coupled with no reporting address is no different from having no DMARC record at all. The addition of a reporting (RUA) address unlocks a crucial point of DMARC—feedback from the internet as to how your domain is being used (for good or bad purposes). This feedback contains information as to how these emails were authenticated—vital information to ensure your emails are correctly configured, which in turn can be used to begin increasing your security policy with confidence.
Our research also found a high number of domains not adhering to general best practices. Issues such as Too many SPF lookups, external DMARC verification errors or over-authorisation of SPF records. All of which add to risk, in the form of your attack surface or deliverability problems if not corrected. Our DMARC Management Platform holistically looks at your email authentication and DNS practices and provides guidance in resolving any issues.
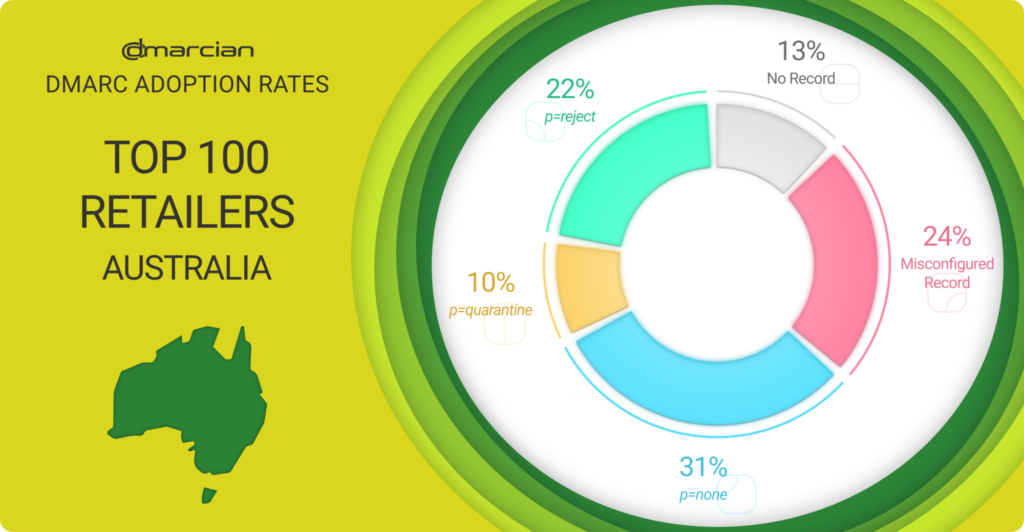
DMARC Status of the Top 100 Australian Retailers
Compared to the APAC top 500 domains, more of Australia’s top 100 retail domains have a DMARC record in place with an enforced DMARC policy of p=quarantine or p=reject with fewer left twisting in the wind with no domain protection.
That said, 68% of domains in this group are not fully protected by DMARC—13% lack a DMARC record, and 31% have a p=none policy. Another 24% have technical errors or aren’t abiding by best practices.
That leaves 32% with enforcement policies that send messages failing SPF and/or DKIM authentication to spam (p=quarantine) or don’t deliver them at all (p=reject)—the latter being the ultimate goal of DMARC deployment.
Recognizing the importance of DMARC in preventing email spoofing, the Australian Cyber Security Centre (ACSC) has released guidelines, Malicious Email Mitigation Strategies and How to Combat Fake Emails, that include specific DMARC implementation recommendations.
Implement DMARC to enhance SPF and/or DKIM: Domain-based Message Authentication, Reporting and Conformance (DMARC) enables a domain owner to specify a policy stating what action the recipient’s email server should take if it has failed a Sender Policy Framework (SPF) check and/or Domain Keys Identified Mail (DKIM) check.
Malicious Email Mitigation Strategies
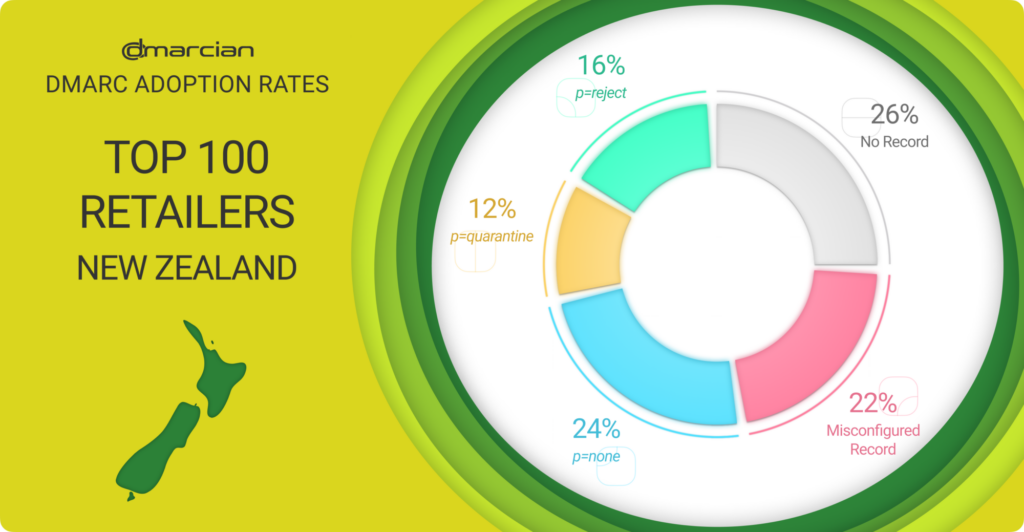
DMARC Status of the Top 100 New Zealand Retailers
From August 30, 2023 to August 30 2024, New Zealanders lost approximately $2.3 billion on online scams, according to the State of Scams in New Zealand report. They also reported that online shopping fraud displaced identity theft as the top reason for financial losses and credited artificial intelligence as a way for criminals to be more productive and illusive.
Similarly, New Zealand’s eCommerceNews reports an increase in bogus online retailers “with nearly 80,000 counterfeit websites detected in 2024 as the holiday shopping season approaches.” These illegitimate websites target New Zealand shoppers by pretending to be brands like Pandora, Swatch, H&M, Princess Polly, and Zara. They look and behave just like the bonafide online shops and trick people into filling their online shopping carts and entering payment card data.
The top 100 New Zealand retail domains align closely with the top 500 APAC retail domains, with 72% of the domain without the full protection DMARC offers. Twenty-eight percent of the domains are covered with p=quarantine or p=reject DMARC policies, though 22% have technical errors or aren’t abiding by best practices.
Written and updated by New Zealand’s Government Communications Security Bureau, the Information Security Manual (NZISM) outlines cybersecurity best practices, including DMARC in section 15.2 Email Infrastructure.
Therein, they advise that DKIM, SPF and DMARC be implemented with a p=quarantine or p=reject policy to protect people from phishing and malware distribution attacks. While NZIM is targeted at government domains, “crown entities, local government and private sector organisations are also encouraged to use this manual.”
Email is a critical tool for communication, and is commonly targeted by cyber-attacks. It is hard to protect because email is historically insecure and subject to social engineering. Email authentication protects your email from impersonation attacks like spoofing and phishing; phishing and malware distribution attacks are common internet security threats. To avoid agency domains being used fraudulently (e.g. for spam or spear-phishing), the following should be implemented: Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), Domain-based Message Authentication, Reporting & Conformance (DMARC) records.
NZISM Section 15.2.5.
DMARC Policy Enforcement Comparison
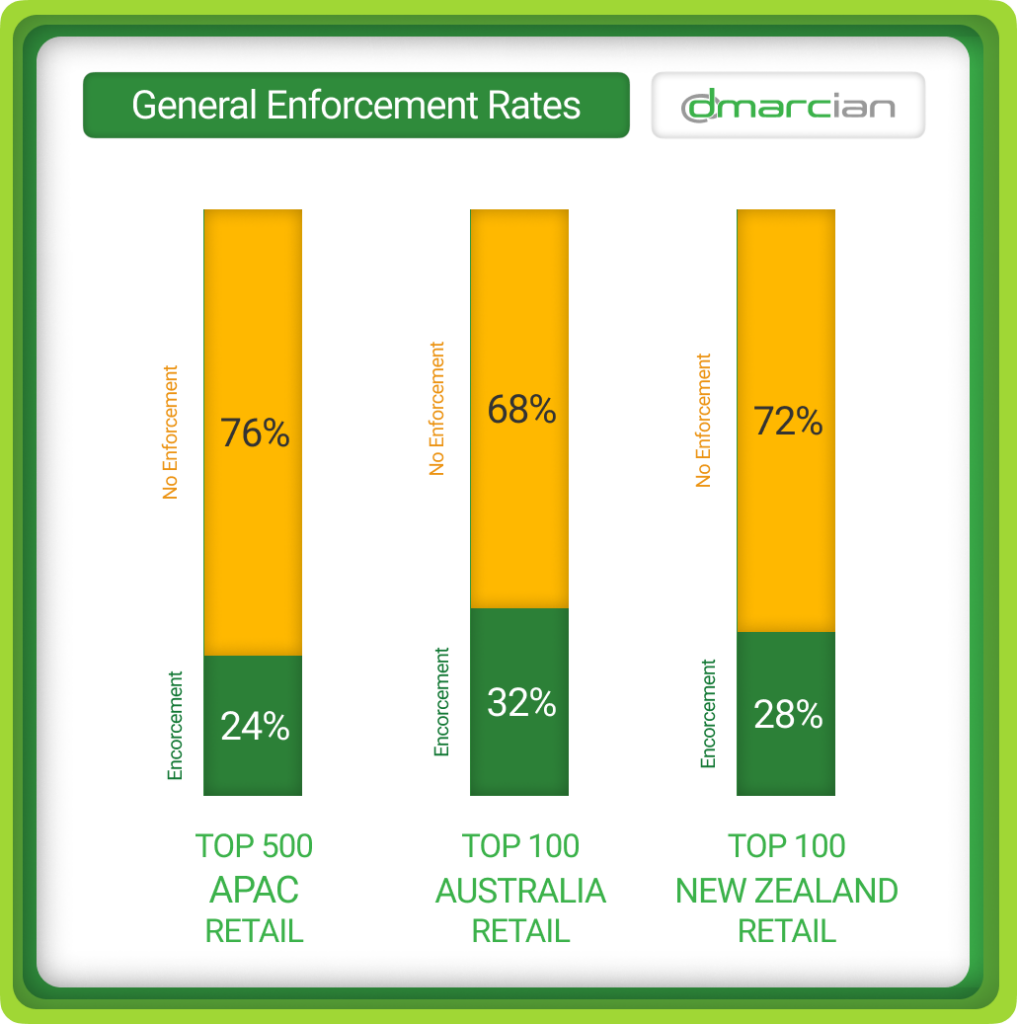
DMARC adoption rates in the APAC region are inconsistent across countries and industries, as we’ve seen in other regions and are affected by DMARC awareness, regulatory pressures and resource availability.
With these low DMARC adoption numbers, it’s fair to say that retailers are yet to understand the value in DMARC. With more money spent on cybersecurity each year, cybercrime keeps increasing—the top attack vector being email-borne. DMARC not only mitigates phishing attacks impersonating your domain coming inbound to your organisation, but it also prevents threat actors from using your domain against your customers as well as those in your supply chain. I have come across scenarios where an organisation adopting DMARC has forced supply chains to correct their own practices, benefiting your entire ecosystem. The big players in the email ecosystem have seen the light and are doing what they can to make the world of email better; however, the crusade is not over. Work is still needed to educate and promote the true benefit of DMARC, a scalable email security policy that provides visibility into how your domain is being used or abused across the internet.
Tass Kalfoglou, Director of dmarcian APAC Business Unit
We’re here to help
While DMARC adoption with an enforcement policy is around 24%, the APAC region lags behind regions like North America and Europe; however, the DMARC uptake is gaining momentum thanks to email industry regulations and a greater understanding of how DMARC is the primary control to observe and restrict email domain usage.
With a team of email security experts and a mission of making email and the internet more trustworthy through domain security, dmarcian and our partners have helped retailers reach DMARC enforcement to keep their customers and brand safe. We’re people helping people secure their domains from phishing and manage their email security for the long haul.
Want to continue the conversation? Head over to the dmarcian Forum.


