
DMARC Adoption among U.S. and Canada Retailers
We’ve seen a brisk uptake in DMARC adoption since Google and Yahoo began enforcing stricter sender requirements in 2024. With that in mind, we’re continuing our DMARC adoption research and taking a look at the top retail domains in the U.S. and Canada based on estimated revenue.
Retailers have always been a popular target for criminals because of the sheer volume and value of personally identifiable information and payment information retailers hold in their databases and networks.

“Phishing and credential harvesting remain a priority all year long as a primary intrusion vector across most cybercriminal operations. Our members report a steady prevalence in phishing attempts with lure themes involving popular product promotions targeting consumers for PII harvesting. Members have also reported increasing imposter websites, product-focused phishing attempts, and phishing attempts impersonating executives.”
—Retail and Hospitality Information Sharing and Analysis Center
American Retail Phishing Scams
Verizon’s 2024 Data Breach Investigations Report discovered that phishing and pretexting via email were the top reason for cybersecurity incidents in the retail sector, with 73% of breaches caused by one or the other or both. They define pretexting “as a stand-in for business email compromise, where attackers leverage existing email chains to convince victims to do something, such as update an associated bank account with a deposit.”
Some of you may remember retail giant Target’s chilling breach as a result of one of its contractors being phished. Their refrigeration contractor in Pennsylvania clicked on a phishing email designed to steal user credentials. When the imposters gained access to Target’s network, they installed malware and began harvesting customer data. The damage from the attack left Target responsible for a massive cleanup, including fines, legal fees, and customer credit monitoring. All told, the damage was around $290 million.
Phishing breaches via a third-party vendor have become all too common, unfortunately. An organization’s cybersecurity posture is only as secure as that of its partners and why vetting and setting up monitoring for third-party vendors is crucial these days.
On that point, DMARC is a bellwether cybersecurity control. When an organization lacks a DMARC record or has one that isn’t at the p=quarantine or p=reject enforcement level, it’s an open invitation for bad actors and signals that the organization might not have a comprehensive cybersecurity program in place.
You can use our free domain audit tool to spot-check the DMARC, SPF and DKIM status of any domain; additionally, you can put our DMARC Management Platform to work if you’d like to continually monitor the DMARC status of your third-party vendors.
DMARC Status of the Top 500 American Retailers
Our research reveals encouraging progress: 74% of the top 500 U.S. retail domains have published a DMARC record aligned with best practices, and we couldn’t be happier! The majority of these domains, thanks to Google and Yahoo to some extent, are advancing their cybersecurity practices by bringing in the primary control to observe and restrict email domain usage: DMARC.
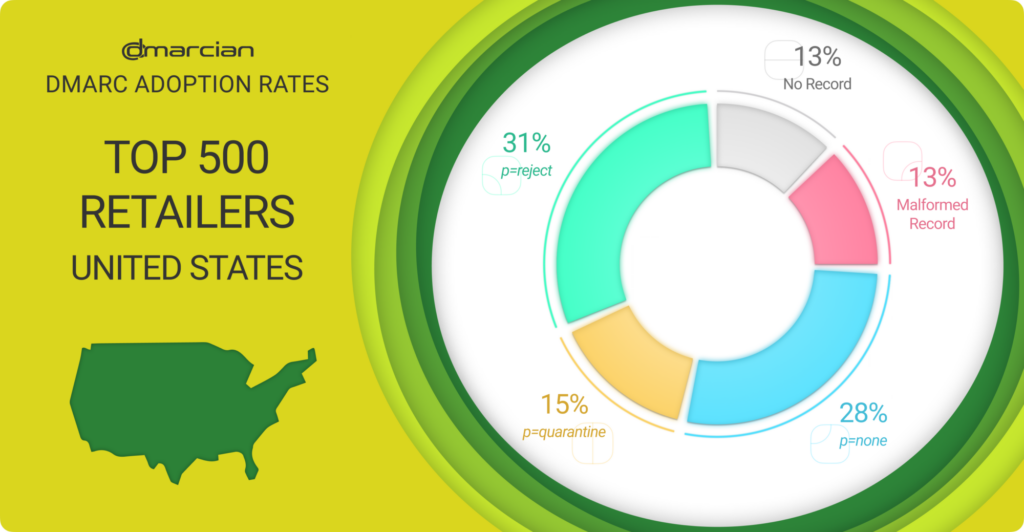
Ok, we could be happier. While 31% of the top U.S. retailers have reached the ultimate p=reject DMARC policy enforcement and 15% have met the penultimate p=quarantine policy enforcement, 28% remain at the monitoring policy of p=none and aren’t taking advantage of DMARC’s power.
Not yet, at least. Optimistically, let’s assume that the p=none cohort has recently begun their DMARC journey and are not resting on their laurels after meeting the modest DMARC requirement handed down by Google and Yahoo.
The remaining 26% of the top U.S. retailer domains are split evenly in two camps—no DMARC record and malformed DMARC records. And when we break down the DMARC adoption data, 46% of the domains have reached DMARC enforcement with p=reject or p=quarantine policies, while 54% have no DMARC record or ones that have mistakes and are laid bare to phishing exploits.
“Fortune 100 customers often have the same problems as a small business and vice versa,” says Fred Bianchi, dmarcian U.S. Business Unit Director. “The customers, verticals, and organization size may vary, but the issues tend to be similar.
Some of those challenges could be SPF record mismanagement, especially over-authorization; DKIM keys that need to be rotated from 1024- to 2048-bit key length; and all too often (especially for smaller businesses), a DMARC record that simply consists of v=DMARC1; p=none; with no RUA. This may solve for minimum requirements to have a DMARC record in place, but it provides zero visibility into data that helps inform decision making and next steps. That data is paramount if the policy is to ever advance to a level of enforcement, and that should be the goal.”
Missing RUA reporting address and SPF records
Continuing the themes in our European and APAC DMARC adoption research, DMARC and SPF record errors accounted for most of the authentication issues in Canada and the U.S.
Related to DMARC records, an average of 12% of the U.S. and Canada domains were missing the RUA tag. This is a problem because without the RUA tag, there’s no email address for sending the DMARC reports that feed our DMARC Management Platform to give you visibility and control over your domains. In this case, the valuable XML reports are lost in the ether, and you can’t see what’s happening with your domains.
As you can see below, the RUA address is the third component of the following DMARC record:

On the SPF front, an average of 26% of the top Canada and U.S. retail domains’ SPF records were missing, malformed, or not following industry best practices. That’s no good because missing and improperly formatted SPF records can lead to failed email authentication and the related deliverability problems for over a quarter of the domains.
“The other problem we often see is when domain owners are trying to ‘work around’ the SPF lookup limit as opposed to following common best practices, which include not adding entries if they are not needed,” continues Fred. “It is never a good idea to authorize senders by SPF when they don’t actually need it. But even when we point this out there are too many times where the domain owner insists on a way to go beyond the 10 lookup limit.”
The most common issue we saw was missing SPF records, followed by SPF syntax mistakes and exceeding the built-in limit of 10 DNS lookups. Here’s our guidance on fixing the 10 lookup limit without using SPF flattening and other work-arounds that can open your domain to more abuse.
Verify that your SPF record has error-free syntax. It also helps you identify third-party senders and IPs authorized to send on behalf of your domain.
DMARC Status of the Top 100 Canada Retailers
When surveying the top 100 Canada retail domains, we found that 43% have published a DMARC record aligned with best practices. This signals familiarity with the control as a way to stop fraudulent emails emanating from their primary domain.
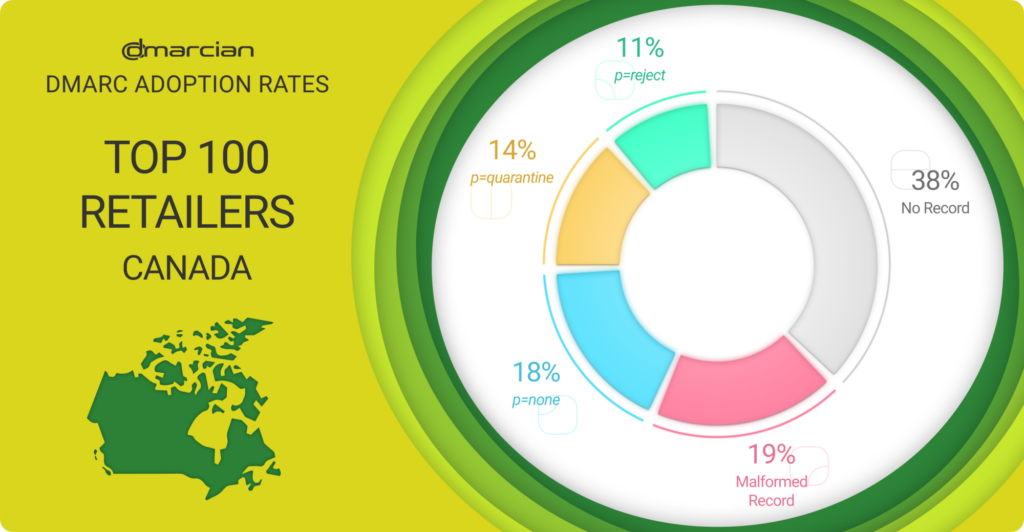
Of these domains with a valid DMARC record, 25% are protected with DMARC policies at enforcement levels with 14% at p=quarantine and 11% at p=reject.
The remaining 75% lack DMARC guardrails and are prone to phishing intrusions because they have no DMARC record; problems with their DMARC record; or a p=none DMARC policy, which provides visibility into emails being sent from a domain but provides no protection from phishing exploits whatsoever.
“In 2023, businesses saw recovery costs from cyber incidents double from $600 million in 2021 to $1.2 billion while preventative spending rose only slightly, from $9.7 billion to $11.0 billion. Given email’s role as a prime attack vector, investing in a solution like DMARC delivers a strong ROI by stopping fraud before it happens. Don’t wait for another forced incentive (like Google or Yahoo’s DMARC requirements) to safeguard your brand and customers. Proactively deploying DMARC now is both cost-effective and crucial.”
—Asher Morin, Toronto-based dmarcian Director of Professional Services
Recognizing the importance of DMARC in fighting phishing and email fraud, the Canadian Centre for Cyber Security’s Implementation Guidance: Email Domain Protection recognizes that with DMARC, “you can reduce a threat actor’s chance of carrying out successful malicious email campaigns. These measures will protect your organization in the following ways:
- Preventing the delivery of malicious messages impersonating your domains;
- Deterring threat actors from attempting to spoof protected domains;
- Improving the security of email recipients; and
- Protecting the reputation of organizations whose domains are the target of spoofing.”
DMARC Policy Enforcement Comparison
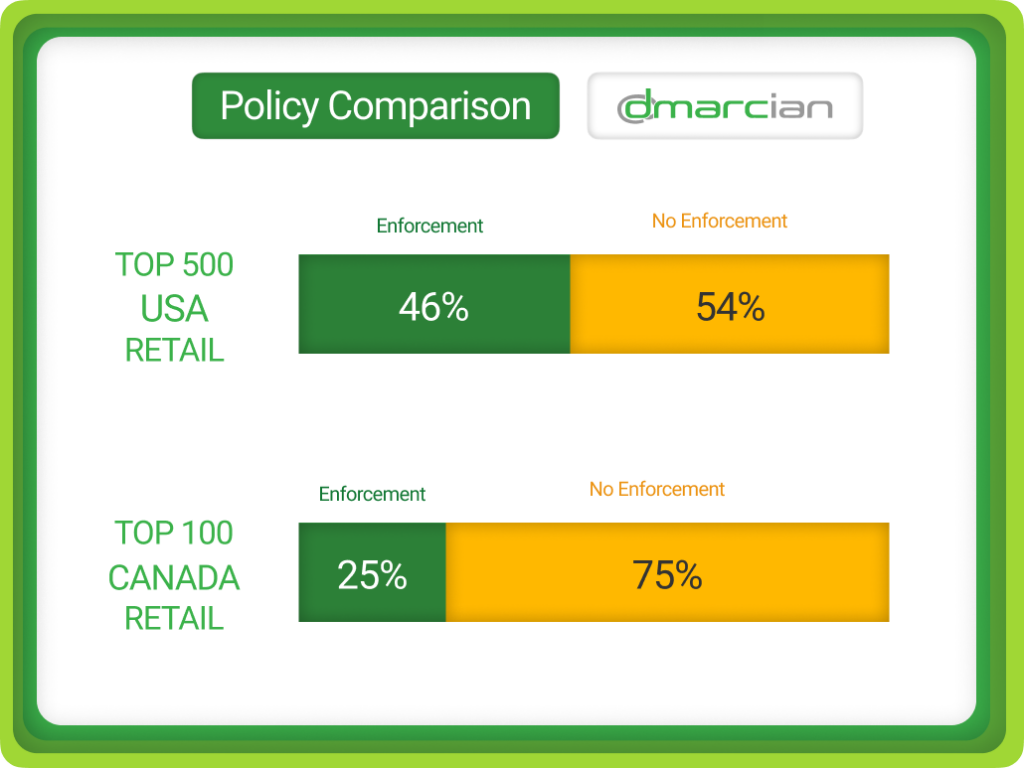
In this DMARC policy comparison, we see that Canadian retailers follow US retailers by 21 percentage points in having a p=quarantine or p=reject DMARC policies. Though DMARC adoption is on the upswing in Canada and the United States, more than half of the retailers in each region are lacking the necessary DMARC policy enforcement levels to keep their customers, employees and vendors safe.
As we mentioned in the opening, Google and Yahoo’s DMARC requirement has certainly contributed to the big boost in DMARC adoption; as a mission-driven organization to spread DMARC across the internet, we appreciate that. However, many organizations aren’t taking the next step in securing their domains with the DMARC policies, p=quarantine and p=reject, that keep fraudulent email out of inboxes.
We’re here to help
With a team of email security experts and a mission of making email and the internet more trustworthy through domain security, dmarcian and our partners have helped retailers reach DMARC policy enforcement to keep their customers and brand safe. We’re people helping people secure their domains from phishing and manage their email security for the long haul.
Want to continue the conversation? Head over to the dmarcian Forum.


