
DMARC Adoption among Japanese businesses
Key Takeaways
- Most Japanese businesses lack DMARC enforcement
- Japan’s regulatory landscape and recent phishing exploits
- SPF errors are common among Japanese domains
- DMARC helps stop fraudulent email and improves deliverability
While Japan is home to lucrative, tech-focused enterprises that are pressing forward to stabilize their cybersecurity postures, DMARC adoption and policy enforcement remain low.
As phishing and email spoofing continue to be among the most common attack vectors targeting all organisations, having the DMARC control in place is no longer optional; it is vital for brand trust and deliverability.
After Google and Yahoo’s orchestrated announcement to require DMARC for bulk senders, Yahoo Japan announced a similar mandate.
To ensure safe and secure use of Yahoo! Mail, we recommend that email senders implement sending domain authentication. Emails that do not implement and pass SPF, DKIM, or DMARC authentication may be classified as spam or rejected. We will strengthen our countermeasures against spoofing and phishing by implementing sender authentication for emails sent from Yahoo! JAPAN when using Yahoo! Auctions and Yahoo! Wallet. We also plan to encourage banks, credit card companies, and other organizations to introduce sender domain authentication technology, striving to maximize the prevention of email-based personal information theft.
Japanese Regulatory Landscape and DMARC
- The Japanese Ministry of Economy, Trade and Industry (METI) asked credit card companies to implement DMARC; this guidance is related to 3D Secure, a broader credit card security program similar to PCI DSS.
- METI also requires semiconductor manufacturers to add DMARC to their transaction conditions to combat email spoofing and enhance supply chain security.
- DMARC is mandatory for Japanese government agencies and consistent with broader unified government IT standards.
- Mailbox providers Google, Yahoo, Yahoo Japan, Apple and Microsoft require DMARC for large senders.
- Japan’s National Police Agency looks to DMARC as a control to stop people from being tricked by fraudulent emails. They are working with other agencies to advocate for DMARC with a p=reject policy.
Active Cyber Defense Law and DMARC
Japan’s Active Cyber Defense Law (ACD) was ratified in May 2025 for government and enterprise networks. In its traffic monitoring element, DMARC reports can provide visibility into email ecosystems to track both legitimate and suspicious email activity so security teams can isolate threats. In the case of ACD’s critical infrastructure incident reporting, where operators must report cyber incidents within 24 hours, DMARC reports provide detailed information and evidence on domain threats like phishing and spoofing.
Phishing Exploits Increase in Japan
In early 2025, Japan businesses were barraged with phishing attacks by cybercriminals employing phishing kits to send malicious email campaigns targeting individuals and organizations across the island country.
As is often the case, the bad actors impersonated high-profile Japanese brands like Amazon, PayPay and Sumitomo Mitsui Card. The fraudulent emails used social engineering tactics to lead people to forged login pages in an attempt to steal login credentials and payment card information. The Japanese police reported a record 1.2 million phishing cases in the first half of 2025, resulting in online banking fraud losses exceeding 4.22 billion yen.
DMARC Adoption among Japan’s Top 250 Companies
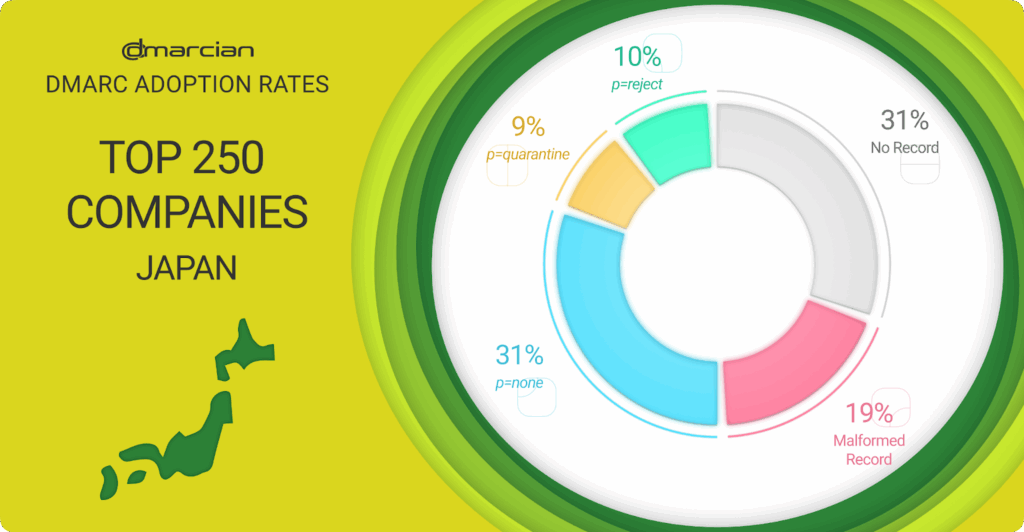
We surveyed the top 250 Japanese companies based on revenue to assess their DMARC and here’s what we discovered:
- 31% have no DMARC record
- 31% have a record at the p=none monitoring, no-enforcement phase.
- 19% do not follow best practices, leaving domains exposed or without visibility.
- 9% have a DMARC policy of p=quarantine, the penultimate policy progression preceding p=reject.
- 10% are at p=reject, taking full advantage of the protection DMARC offers.
From this data, we see that 81% of the top Japanese companies are not protected from being used in email exploits. The parent domains of these organisations lack DMARC records; contain mistakes in their records; or reflect a p=none DMARC policy, the monitoring phase that doesn’t provide enforcement for emails that fail authentication.
Ten percent of the businesses have achieved a p=reject DMARC enforcement policy and are fully protected; nine percent reflect the p=quarantine policy where failing emails are sent to the spam folder.
After Google and Yahoo instituted the DMARC requirement for bulk senders, domain owners across the globe rushed to publish a DMARC record with a p=none policy to meet the baseline requirement. To this day, many bulk sender domains remain perched at the monitoring policy of p=none without seeming to understand the benefits of p=quarantine and p=reject DMARC enforcement policies.
In thinking about Japan’s enforcement policy deficit, we have to wonder if this p=none-is-good-enough phenomenon is in effect with the companies we surveyed. In time, whispers the email ecosystem, the big email players will continue to make email safer and reduce spam by introducing a requirement to enforce DMARC policies.
Japanese Challenges with DMARC Adoption
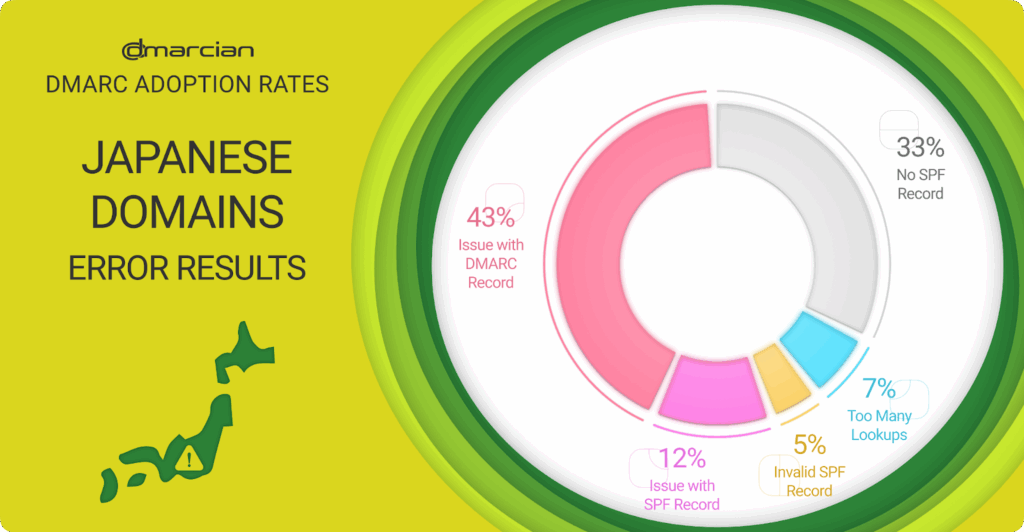
When we calculated the errors we found in our Japanese domain research, we observed that 33% of the domains lack an SPF record entirely; another 43% suffer from faulty DMARC records, leaving a vast majority susceptible to email authentication failures. When we break down SPF record issues, we find that 12% have errors, 7% exceed the DNS lookup limit and 5% have invalid syntax.
- 33% lack SPF records
- 43% have faulty DMARC records
- 12% have SPF record errors
- 7% have SPF records that exceed the SPF lookup limit
- 5% have invalid SPF records
Does your SPF record have valid syntax and is it free of errors? Errors can lead to diminished email deliverability and failed email authentication.
Why is DMARC essential?
When strong security controls like DMARC are deployed against fraudulent email, deliverability is improved, brand trust is upheld, and visibility is granted to domain owners. Organizations with a DMARC record with an enforcement policy of p=quarantine or p=reject, along with DMARC requirements for their third-party vendors, contribute to a safer email program and supply chain operations.
Japanese customers have a high attention to detail, and are also very cautious in adopting new technologies. This is especially true for a security control such as DMARC, where a mistake can result in customers missing important communications. We have a Japanese Data Center, regional support and local partnerships with experts ready to help the Japanese enterprises adopt DMARC confidently.
—Tass Kalfoglou, dmarcian APAC Director
How dmarcian can help
Effective DMARC deployment and maintenance is crucial in fighting phishing and spoofing, and we offer the resources and expertise you need to get it right the first time.
We help organisations of all sizes:
- Deploy DMARC the right way—no guesswork, no disruptions
- Gain full visibility into your email ecosystem
- Stay ahead of evolving email security policies
Want to continue the conversation? Head over to the dmarcian Forum.


