
Using the “envelope_to” Domain to Discover Source Owners
Our support specialists get customer question about emails that mysteriously fail DMARC authentication checks and wondered how they might untangle the conundrum.
We showed a customer who uses Microsoft Office 365 for organizational email the envelope_to domain in our DMARC Management Platform. After we shed light on the envelope-to domain, the customer was able to investigate and understand what had happened with the failures.
Because many of our customers utilize Microsoft enterprise email, which started sending DMARC reports in 2023, we thought we’d take this customer support case as a basis for exploring how to gain insights from the envelope_to domain in RUA reports.
Learn about RUA reports, the information they contain, and how they differ from RUF reports.
What is an envelope_to domain?
An envelope_to domain is the domain of the email address to which an email is sent. In the email address [email protected], example.com is the envelope_to domain. The envelope_to field is optional for receivers to include in RUA reports, and Microsoft is one of few receivers that include it.
How you can leverage the envelope_to domain
The envelope_to domain can be useful in gaining an understanding of why some legitimate traffic is failing DMARC when other troubleshooting tactics aren’t definitive. It can provide insight into a vendor that is sending email on your behalf or an individual that is on the receiving end of the email. You can also use the envelope_to domain to search incoming mail logs for tracing an email. For example, if you use the envelope_to domain to perform an email trace in your inbound email logs, you can find out which person or group within your company is using a source.
Where to find the envelope_to domain in your dmarcian account
In the past, you needed to examine raw RUA reports to locate the envelop_to domain; now, we’ve made it a lot easier for you. All you need to do is navigate to the Detail Viewer, expand a source, and activate the envelope-to column via the Columns Visible function.
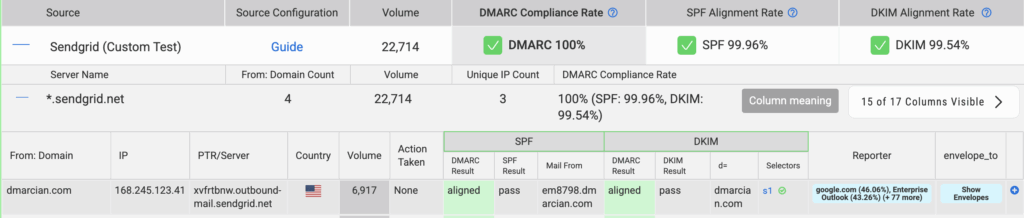
To examine envelope_to domains, simply click the Show Envelopes button you see on the far right in the image above.
To bring this story full circle, once the customer saw that the envelope_to domain was from a vendor/customer, they knew what system was responsible for sending the emails. They were able to set up DKIM signing so these emails can be DMARC compliant.
In another, similar case, a customer was able to determine that email failing DMARC was sent internally because of the envelope_to domain; they were able to do a message trace for incoming emails to get a message sample. They could now set up the source to send DMARC-compliant email.
Microsoft mandates DMARC, SPF, DKIM for large senders in their consumer email services outlook.com, hotmail.com and live.com.
DMARC and dmarcian can help
dmarcian’s mission is to see universal DMARC adoption. We advocate for the technology and advance it by helping organizations of all shapes and sizes deploy it. We’ve learned that a properly structured DMARC deployment can lay the foundation for an organization’s trustworthy online presence.
We’re here to help you assess your domain catalog and implement and manage DMARC for the long haul. You can register for a 30-day trial where our onboarding and support team will help you along the way.
Want to continue the conversation? Head over to the dmarcian Forum.


