
The State of DMARC in Switzerland
Email-borne cyber threats are evolving and becoming more polished and undetectable, especially when criminals use AI to develop and deploy phishing and brand impersonation exploits. The case is no different in Switzerland.
Swiss residents reported 975,309 phishing incidents to Switzerland’s National Cyber Security Centre (NCSC) antiphishing.ch reporting platform—a 79% increase from 2023. The NCSC also observed a 108% increase in phishing websites.
In order to make phishing sites as credible as possible, criminals often impersonate well-known brands, companies and public entities. 338 brand names were appropriated by criminals for phishing attacks; of those, Swiss brands comprised 64% of the total, while the remainder were non-Swiss brands.
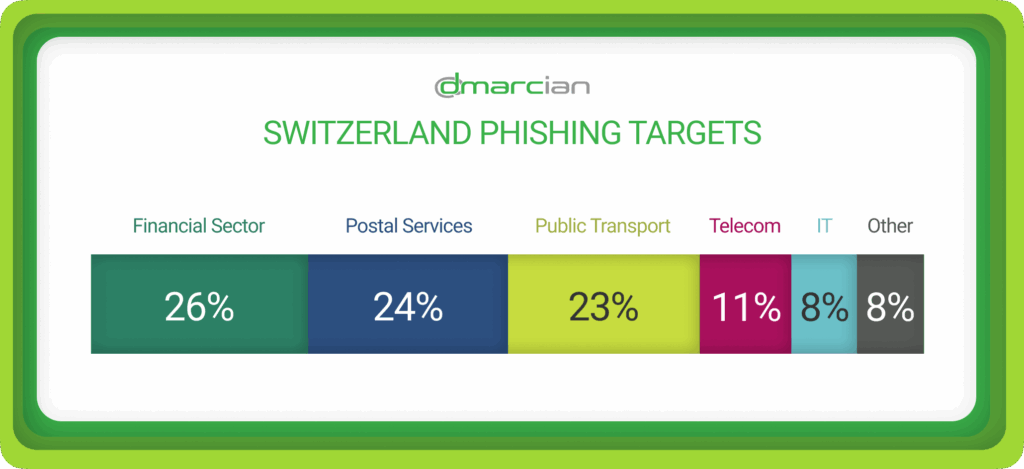
The financial sector, postal services, public transport, telecommunications and IT are the most commonly targeted sectors for phishing. These proportions remained relatively constant from month to month.
Data Breaches in Switzerland
To set the stage for our research, we looked at Swiss domain-based data breaches and learned that phishing and spam messages continue to be two of the most frequently reported incidents according to the Swiss Federal Office for Cyber Security.
In one of Switzerland’s recent data breaches, criminals employed phishing and supply chain exploits to carry out a ransomware attack against Radix Swiss Health Foundation, a Zurich-based non-profit health education organisation. The ransomware group Sarcoma used the common tactic of phishing to gain network entry then exploited third-party vulnerabilities to ultimately steal over a terabyte of federal documents and PII. These scans, contracts, financial data, and correspondences were then posted on the dark web and available for free.
DMARC Adoption among Swiss Banks
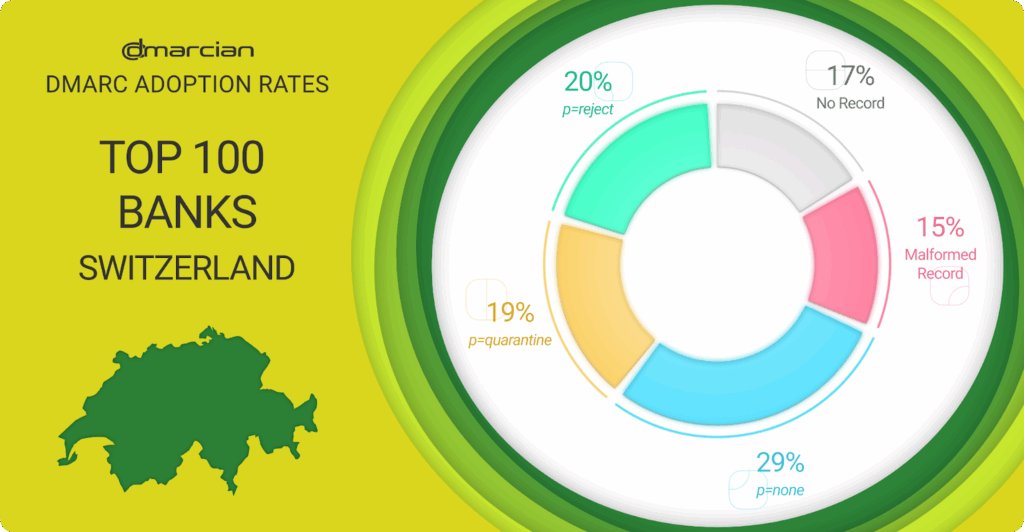
We examined the parent domains of the top 100 Swiss banks categorized by revenue. Here’s what we found:
- 17% have no DMARC record
- 29% have a record at the p=none monitoring, no-enforcement phase.
- 15% do not follow best practices, leaving domains exposed or without visibility.
- 19% have a DMARC policy of p=quarantine, the penultimate policy progression preceding p=reject.
- 20% are at p=reject, taking full advantage of the protection DMARC offers.
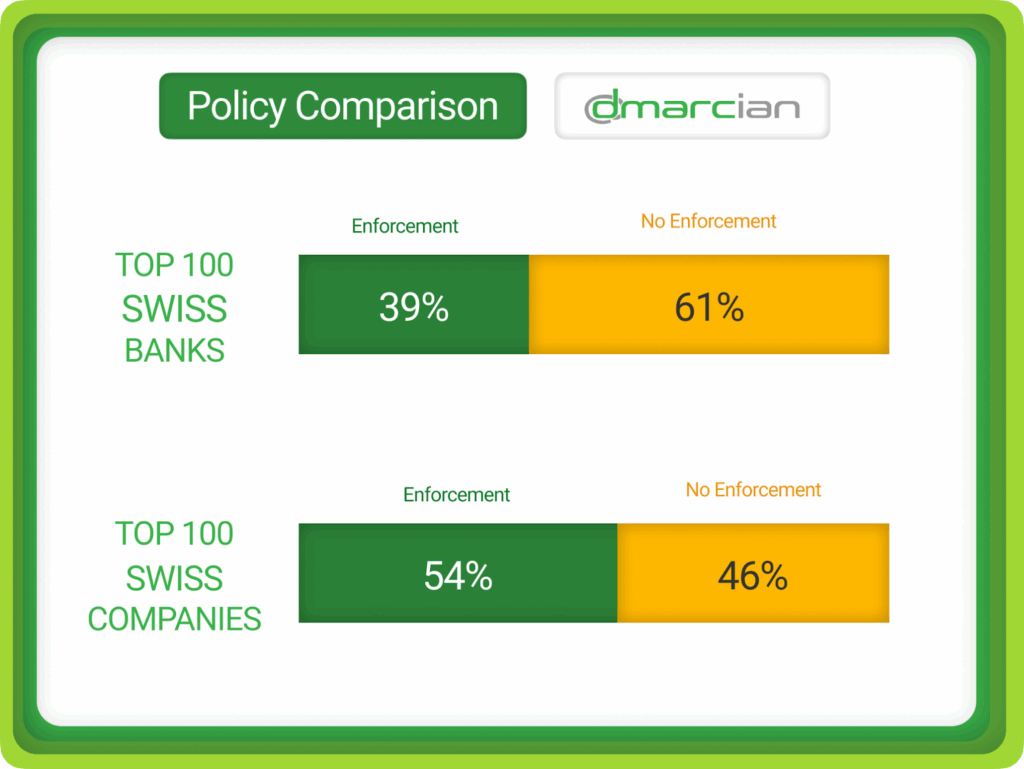
As we consider these data points, we see that 61% of the top 100 Swiss banks are not protected from being used in email exploits. They have no DMARC record; mistakes in their records; or a p=none DMARC policy, the monitoring phase that doesn’t provide enforcement for emails that fail authentication. 20% of the banks have achieved p=reject and are fully protected by DMARC enforcement; 19% reflect a p=quarantine policy where failing emails are sent to the spam folder.
DMARC Adoption among Swiss Businesses
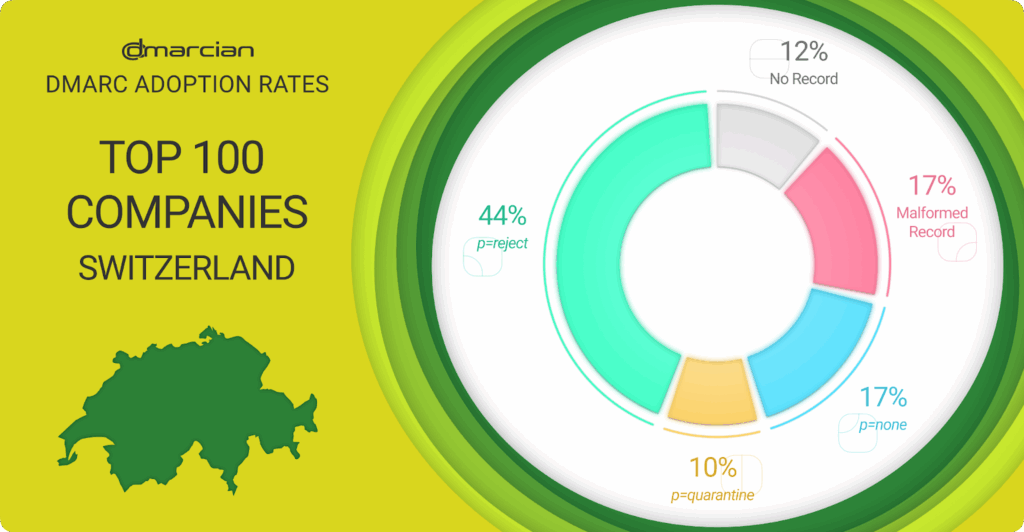
As with the top banks, we studied the top 100 Swiss organisations’ parent domains by revenue to arrive at the following results:
- 12% lack a DMARC record
- 17% are at the p=none DMARC policy
- 17% have issues with their records
- 10% have a p=quarantine DMARC policy
- 44% are at p=reject
As you can see, with the top 100 Swiss companies we find an improvement in DMARC adoption and enforcement compared to banks. Still, 46% are lacking the necessary controls to protect their domains while 54% have achieved DMARC enforcement policies of p=quarantine or p=reject.
SPF and RUA Concerns
In both datasets, we saw that domain operators had trouble adhering to SPF lookup limits and valid SPF syntax. Another common DMARC blunder we observed is the lack of an RUA reporting address. This address determines where DMARC reports are sent and without one, there’s no visibility into the email or its authentication outcome.
Swiss Compliance Landscape and DMARC
Though Switzerland interests haven’t yet mandated DMARC for any business or government sectors, senders must abide by the requirements released by Google, Yahoo, Microsoft, Apple and other email players.
DMARC-related mandates include NCSC’s reporting requirements for cyber attacks on critical infrastructure and Swiss Financial Market Supervisory Authority (FINMA) cyber risk guidance, which includes an obligation for cyber attack reporting.
In both of these cases, DMARC comes into play not only by protecting sensitive financial data from pervasive email threats but also by providing visibility into the email attack surface by receiving and processing RUA and RUF reports. The visibility these reports provide can improve detecting and responding to email threats and provide evidence in meeting the tight 24-hour reporting window in both regulations.
DMARC helps organisations align with general data protection and cybersecurity best practices, which is particularly important for those who also operate within the EU in relation to GDPR.
Why DMARC Is Critical for Swiss Organisations
When strong security controls like DMARC are deployed against fraudulent email, deliverability is improved, brand trust is upheld, and visibility is granted to domain owners. Organisations with a DMARC record of p=quarantine or p=reject in place, along with DMARC requirements for their third-party vendors, contribute to a safer email program and supply chain operations.
One of our customers with 17,000 employees in 100 countries reported a significant improvement after deploying DMARC:
We went from over 75% of illegitimate email traffic to less than 5%. Our IT management recognizes the benefit of DMARC and dmarcian. With the dmarcian dashboard, it was easy to highlight the progress in protecting our domain.
—Switzerland-based global agricultural merchant and processor
dmarcian can help
We know that proper DMARC deployment is key, and we offer the superior tooling and expertise you need to get it right the first time. We help organisations of all sizes:
- Deploy DMARC the right way—no guesswork, no disruptions
- Gain full visibility into your email ecosystem
- Stay ahead of evolving email security policies
Want to continue the conversation? Head over to the dmarcian Forum.


