
2025 Verizon Data Breach Investigations Report: Third-party Breaches Double
Verizon has released the eighteenth edition of their Data Breach Investigations Report (DBIR) covering cyber incidents taking place between November 2023 and October 2024 and representing victims from 139 countries.
In the 2025 report, Verizon’s team analyzes 22,052 security incidents, including over 12,000 confirmed data breaches in organizations of all sizes and verticals. The authors note that the 2025 report “represents the highest number of breaches ever analyzed in a single report.”
Although the threat landscape can vary somewhat due to organizational size, mission and location, there are always certain overarching themes that seem to predominate our dataset regardless of any of these variables. This year is no exception. Possibly the most obvious and noteworthy among them is the role that third-party relationships play in how and why breaches occur.
Verizon 2025 Data Breach Investigations Report
Third-party affiliation breaches
Doubling from last year, 30% of breaches were connected to third-parties. An organization’s third-party software and vendors generally increase its data breach paths, and we’re hearing more and more about vendor-related breaches. You’ll remember the massive SolarWinds and Kaseya supply chain attacks, where many organizations are still recovering from financial and reputational damage.
In these breaches, researchers found that a significant number of them were characterized by credential reuse in third-party ecosystems. Though a particular organization may execute ideal cybersecurity practices, said organization is only as resilient as its connected third-party vendors, whether it be an invoicing service, a file transfer software or a managed service provider.
With supply chain attacks on the rise, it’s critical that organisations in a supply chain have their domains locked down from phishing exploits.
Exploitation of vulnerabilities
A steadily growing liability, there was a 34% uptick in criminals exploiting vulnerabilities for initial network access to carry out breaches. “What is exploitation of vulnerabilities?” you might ask. It’s a rather broad term that describes criminals discovering and leveraging flaws in software, hardware, or networks, especially ones that aren’t yet known or patched, to gain access to systems and data. This method has become a significant initial access vector for breaches, accounting for 20% of all incidents.
Ransomware persistence and growth
Another area of growth, unfortunately, is ransomware. Though there is some good news you’ll read in a second, Verizon researchers found a 37% increase in the presence of ransomware from last year’s report. It was present in 44% of the breaches they reviewed, up from 32% in 2024.
The good news: 64% of organizations affected by ransomware refused to pay the ransome—that’s up 50% from 2023. Additionally, the median ransom payment decreased to $115,000, down from $150,000 from 2024.
Ransomware is also disproportionally affecting small organizations. In larger organizations, Ransomware is a component of 39% of breaches, while SMBs experienced Ransomware-related breaches to the tune of 88% overall.
—Verizon Data Breach Investigations Report
DBIR authors note that ransomware represents the monetization of system access—about 42% of data breaches incorporate compromised credentials, exploited vulnerabilities or the use of phishing.
In their Stop Ransomware guide, CISA recommends implementing “DMARC policy and verification to lower the chance of spoofed or modified emails from valid domains. DMARC builds on the widely deployed SPF and DKIM protocols, adding a reporting function that allows senders and receivers to improve and monitor protection of the domain from fraudulent email.”
DMARC allows domain owners to protect their domains from unauthorized use by fighting ransomware’s common delivery by email.
Business Email Compromise
Not surprising, Business Email Compromise (BEC) continues to be a choice method for financial transfer fraud. Verizon reports that while the number of BEC attacks is increasing, the median amount of money stolen is leveling at around $50,000. BEC tactics, however, are evolving and criminals are taking time to build relationships to leverage.
In our opinion, the really interesting thing about these types of attacks is not simply the scale of them but also the amount of time attackers seem to be dedicating to building familiarity with the victims. AI enthusiasts would, of course, state vehemently that this is solely due to AI tools, but in reality, the trend has simply been going on too long for AI to take all the credit.
—Verizon 2025 Data Breach Investigations Report
Wire transfer made up the majority of BEC proceeds at 88%, while other financial grabs, like digital currency, are being used less.
DMARC is a control that stops forged email so people don’t have to decide if it’s real or a scam.
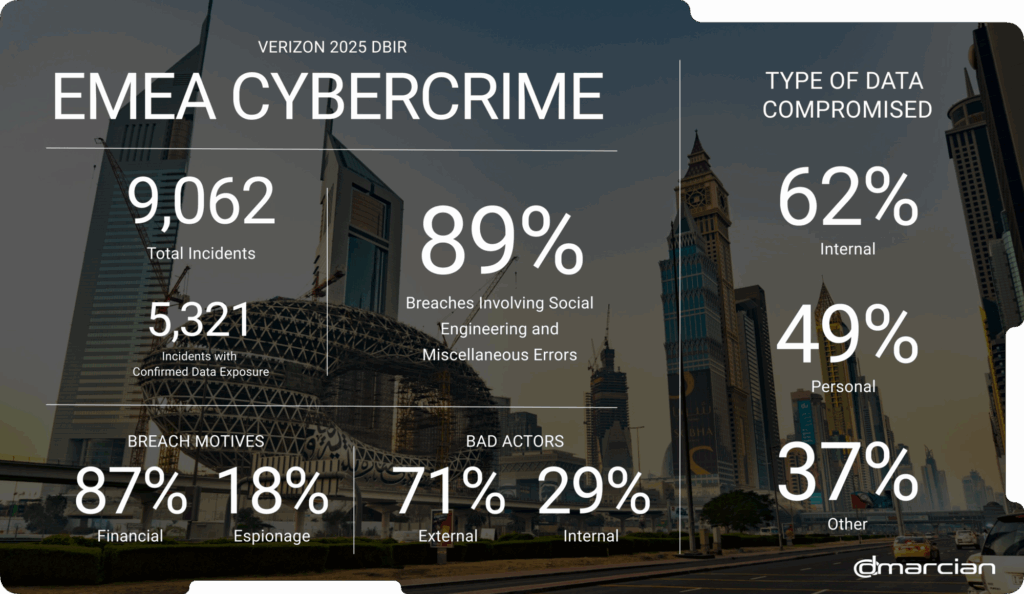
Cybercrime in EMEA
The leading breach types in the Europe, Middle East and Africa region remained consistent with 2024’s DBIR, though the distribution was in flux. System Intrusion increased, accounting for 53% of breaches, up from 27% from last year’s report.
Ransomware attacks, credential theft, and the exploitation of vulnerabilities are likely the blame for this rise. In some minor but good news, social engineering decreased two percentage points to 22%.
Cybercrime in APAC
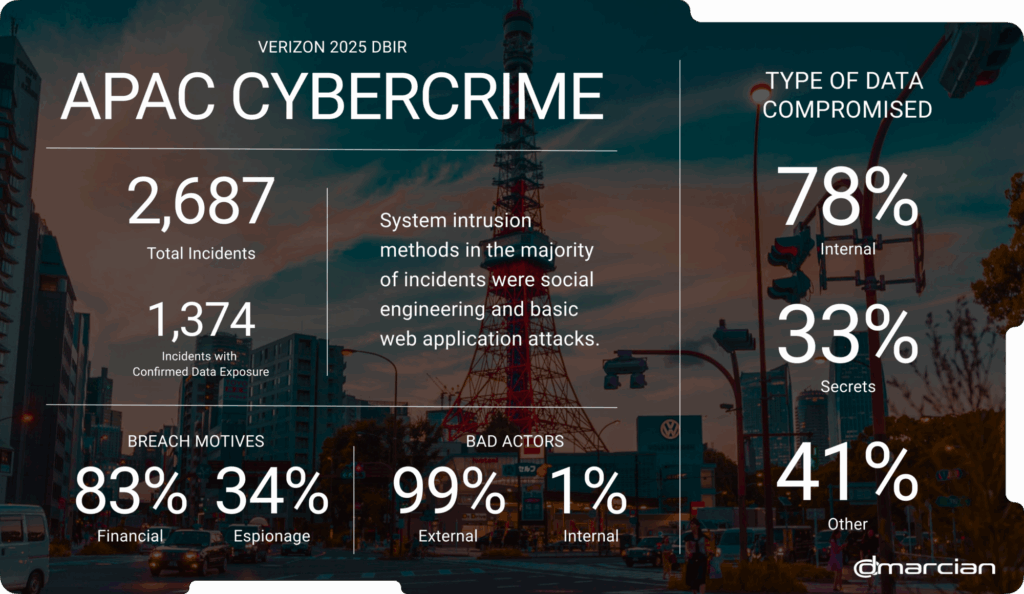
In the Asia-Pacific region, stolen credentials and vulnerability exploitation top the list of breach types. Stolen credentials, commonly hijacked with phishing exploits, were used in 55% of breaches.
Vulnerabilities like unpatched systems, software bugs and misconfigurations were exploited and made up 37% of breaches. Criminals commonly leverage these two penetration practices to carry out ransomware exploits.
The social engineering category accounted for 25% of the breaches in APAC. Business Email Compromise constituted 40% of social engineering breaches; prompt bombing was involved in 34%; and phishing, as always, was widespread, representing 26% of social engineering incidents.
How DMARC and dmarcian can help
DMARC comes into play by helping to protect internet domains from criminals using social engineering and phishing attacks. It ends up being the glue that lets organizations manage email as a domain-based service.
DMARC’s utility as an anti-spoofing technology stems from a far more significant innovation; instead of attempting to filter out malicious email, why not provide operators with a way to easily identify legitimate email? DMARC’s promise is to augment the “filter out bad” email security model with a “filter in good” model.
dmarcian’s mission is to see universal DMARC adoption. We advocate for the technology and advance it by helping organizations of all shapes and sizes deploy it. A properly structured DMARC deployment can lay the foundation for an organization’s trustworthy online presence.
We’re here to help you assess your domain catalog and implement and manage DMARC for the long haul.
Want to continue the conversation? Head over to the dmarcian Forum.


