
Google Groups Security Vulnerability
Recent discussions in the email security ecosystem have highlighted a security loophole concerning Google’s handling of emails sent to a Google Group. This issue arises particularly when the emails come from a domain with a DMARC policy set to p=quarantine or p=reject.
Google Groups functions similarly to a mailing list. When a group address receives an email, Google forwards a copy to each group member, retaining the original From: header. This From: header is crucial, as it’s what recipient systems use to determine which domain to check against for DMARC compliance. In essence, when Google forwards these emails, it’s as if Google is spoofing the domain being forwarded. This becomes problematic with domains like AOL or Yahoo, where the receiving system will reject the email, recognizing that Google isn’t authorized to send on their behalf.
How scammers exploit Google Groups’ email forwarding
- Domain Acquisition: Scammers start by acquiring a new domain and setting up a DMARC policy of p=quarantine or p=reject.
- Sending Emails: They then send emails from this domain to various Google Group addresses.
- Google Address Rewriting: When these emails reach Google groups, Google automatically rewrites the from: address to match the Google Group’s instead.
- Misleading Reply-To Address: The original sender’s (scammer’s) domain is sneakily included in the Reply-To address.
- Passing Authentication: Due to Google’s rewriting, the emails pass SPF and DKIM authentication checks and appear legitimate.
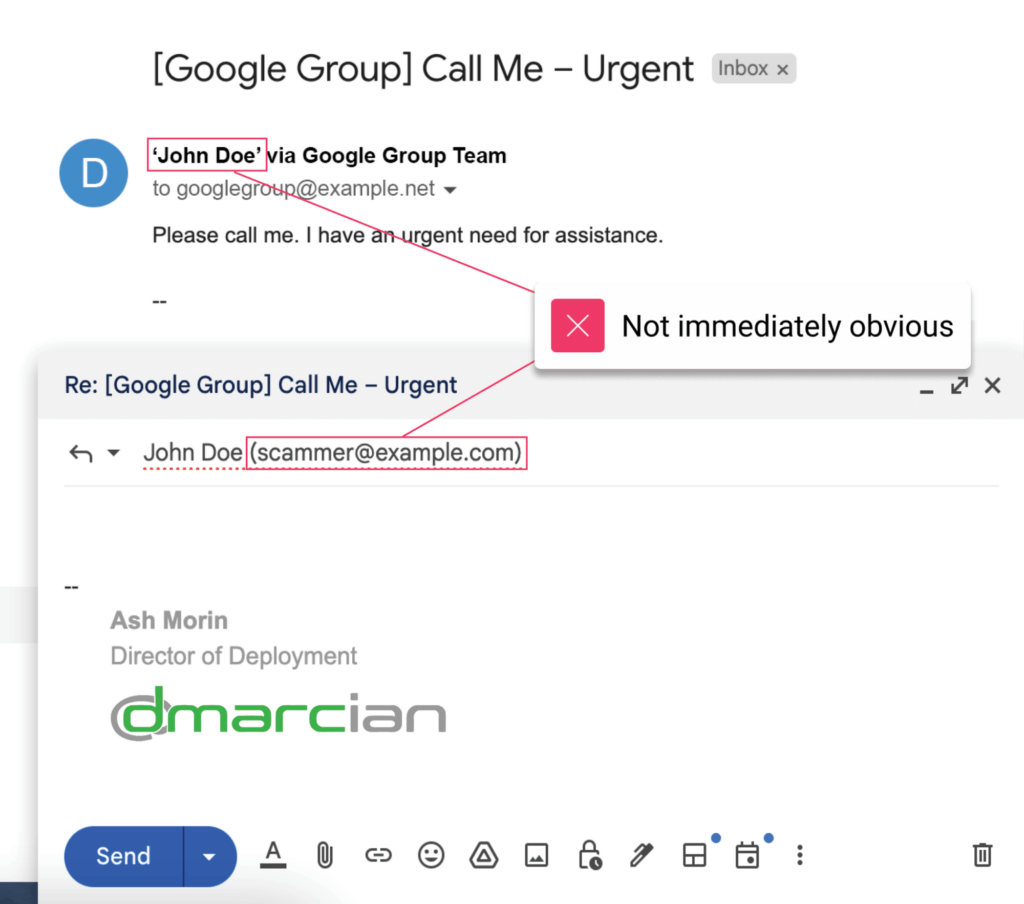
This method exploits Google’s email handling to pass all email authentication standards using the “via” feature to create a false sense of legitimacy with a goal to deceive recipients.
This issue first became prominent in 2014 when AOL and Yahoo adopted a p=reject DMARC policy. Google responded by altering how Google Groups handle forwarded emails from domains under DMARC protection. They started rewriting the “from” address to match the group’s address, adding a “reply-to” header for the original sender’s address. This approach isn’t exclusive to Google; many mailing list servers, including L-Soft’s LISTSERV email list management software, have adopted similar practices.
The concerns about this behavior were raised nearly a decade ago. What’s changed since then? For starters, there’s been increased visibility and adoption of DMARC, partly driven by initiatives like U.S. BOD 18-01, which underscores DMARC’s importance.
So, what does this mean for you? The responsibility largely falls on the shoulders of Google Groups and mailing list owners. If you’re managing a Google Group, consider the following:
- Evaluate whether a Google Group is the best choice versus a shared mailbox.
- Assess the necessity of having the group public. Restricting posts to members of your organization might be safer.
- Increase user awareness. Implement a training module to help your employees exercise caution when receiving emails “via” another address.
Ultimately, ask yourself, “Would I use a mailing list to manage critical email channels for my organization?” If the answer is no, then it’s probably best to steer clear of using a Google Group for such purposes.
If you have any questions, please feel free to get in touch with us.
With a team of email security experts and a mission of making email and the internet more trustworthy through domain security, dmarcian is here to help assess an organization’s domain catalog and implement and manage DMARC for the long haul.
Want to continue the conversation? Head over to the dmarcian Forum.


