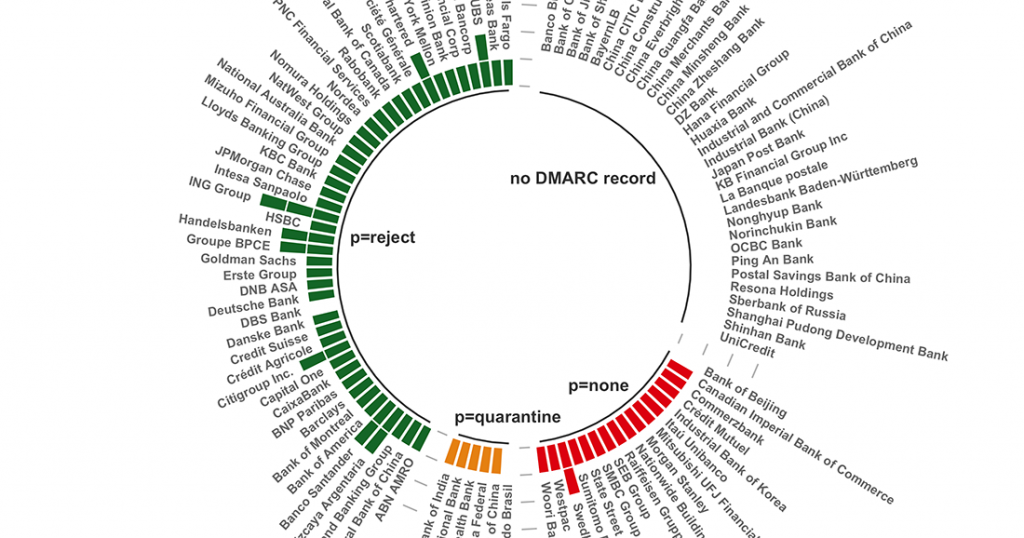
DMARC Status of Top 100 Global Banks – Revisited
Editor’s note: This article was updated June 21, 2023, to include information on the DMARC mandate in PCI DSS v4.0, scheduled for release March 2025.
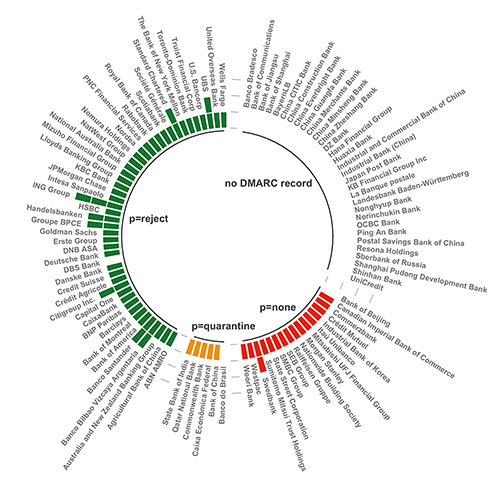
In the second quarter of 2021, we investigated DMARC adoption among the world’s top 100 banks based on assets as reported. A year later, we ran the numbers to see how DMARC adoption is faring in the highly targeted financial services sector.
Here’s what we learned:
- 28% increase of DMARC policies set to p=reject
- 200% increase of DMARC policies set to p=quarantine
- 29% decrease of DMARC policies set to p=none
- 18% decrease of companies lacking a DMARC policy
The trends we observed illustrate an optimistic progression of DMARC compliance in the growth of p=quarantine and p=reject policies. Banks and financial institutions are using DMARC and its underlying technologies as domain-based controls to address:
- Email Fraud – DMARC’s original use-case. DMARC provides visibility of how a domain is used and prevents unauthorized senders from sending email on behalf of an organization.
- Email Reliability – Organizations need email to be reliable. DMARC is the foundation for email delivery, and is often the first step taken to resolve email delivery issues.
- Compliance – Industries, governments, and regulations are increasingly requiring DMARC to be in place. It is also becoming a requirement for many cybersecurity insurance providers.
These controls are more important than ever. In their most recent Phishing Activity Trends Report, the Anti-Phishing Working Group (APWG) reported that in Q1 2021, “phishing attacks against the financial sector, which includes banks, remained the largest set of attacks, accounting for 23.6 percent of all phishing.”
In addition, in Q1 2022 APWG “observed 1,025,968 total phishing attacks. This was the worst quarter for phishing that APWG has ever observed, and the first time that the quarterly total has exceeded one million.”
Payment Card Industry DMARC Mandate
The Payment Card Industry Security Standards Council (PCI SSC) has announced that “The DMARC requirement is a best practice until 31 March 2025, after which it will be required and must be fully considered during a PCI DSS assessment.”
The PCI SSC focuses its work on global payment account data security and develops standards and support services that drive education, awareness, and effective implementation by stakeholders.
When developing anti-phishing controls, entities are encouraged to consider a combination of approaches. For example, using anti-spoofing controls such as Domain-based Message Authentication, Reporting & Conformance (DMARC), Sender Policy Framework (SPF), and Domain Keys Identified Mail (DKIM) will help stop phishers from spoofing the entity’s domain and impersonating personnel.
PCI Data Security Standard Requirements and Testing Procedures, Version 4.0
With this mandate coming in 2025, we’ll be checking in on DMARC adoption in the financial industry to see how the PCI SSC DMARC requirement is affecting DMARC adoption. It has potential far-reaching implications as the PCI DSS requirements apply to the cardholder data environment (CDE), which includes the following:
- System components, people, and processes that store, process, and transmit cardholder data and/or sensitive authentication data
- System components that may not store, process, or transmit cardholder data (CHD) / Sensitive Authentication Data (SAD) but have unrestricted connectivity to system component that store, process, or transmit CHD/SAD
- System components, people, and processes that could impact the security of the CDE.
RELATED: Take a look at DMARC adoption rates for other sectors
We’re Here to Help
With a team of email security experts and a mission of making email and the internet more trustworthy through domain security, dmarcian is here to help assess an organization’s domain catalog and implement and manage DMARC for the long haul.
You can get in touch with us or register for a free trial where our onboarding and support team will help you along the way.
Want to continue the conversation? Head over to the dmarcian Forum.


