
Understanding CISA BOD 25-01 DMARC Requirements for Microsoft 365 and Google Workspace
Nested in the Secure Cloud Business Applications (SCuBA) project, “Binding Operational Directive (BOD) 25-01: Implementing Secure Practices for Cloud Services Required Configurations” provides secure baselines for configuring Microsoft 365 and Google Workspace in the United States’ Federal Civilian Executive Branch (FCEB).
The Cybersecurity and Infrastructure Security Agency (CISA) established the SCuBA project in 2022 to address cybersecurity and visibility gaps exposed by software-as-a-service (SaaS) cyber intrusions and compromises. Although its primary goal is to help secure FCEB information in cloud environments, all organizations can use SCuBA to strengthen SaaS security. —CISA
Following are BOD 25-01’s DMARC baseline configurations required for the FCEB and recommended for all government agencies:
Microsoft 365 Exchange Online baseline configurations
The following required SCuBA Secure Configuration Baselines (SCBs) for Microsoft 365 helps protect federal digital assets with consistent, effective and manageable security configurations:
- An SPF policy for each domain that fails all non-approved senders.
- A DMARC policy for second-level domains (in example.com, example is the second-level domain).
- A DMARC enforcement policy of p=reject.
- The DMARC point of contact for RUA (aggregate) reports must be the email protected.
Gmail baseline configurations
Similarly, the following SCBs are required for Gmail:
- A DMARC policy for second-level domains.
- A DMARC enforcement policy of p=reject.
- The DMARC point of contact RUA reports include [email protected].
- An agency point of contact for RUA and RUF reports.
Expanding Impact: Why BOD 25-01 Mandates Affect Federal Partners and the Entire Email Ecosystem
Do you think these baselines don’t apply because you’re not in government? You might reconsider. If your organization supports federal agencies or collaborates with public sector partners, you could be expected to meet the same rigorous email authentication standards. What begins with .gov doesn’t stay there—these requirements are quickly expanding into sectors like healthcare, finance, and insurance. And as .gov domains become harder to spoof, cybercriminals will shift their focus to less protected targets—potentially yours.
The DMARC-related baselines in BOD 25-01 align with email ecosystem sender mandates. Microsoft, Google, Yahoo, Apple and others now require authentication for senders. The multiple, widespread domain security directives and recommendations, like BOD 18-01, CMMC and Fedramp, signal a coordinated push to elevate email security across both public and private sectors.
DMARC Adoption Progress Among US Government Domains
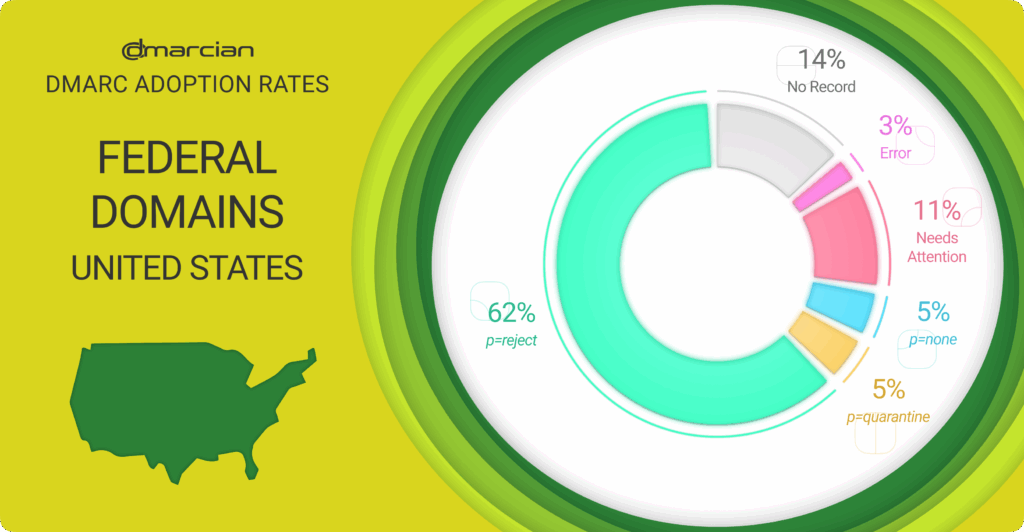
With mandates like BODs 18-01, 25-01 and other directives and guidance, over half of US agency domains are immune from fraudulent email being sent from their domains. Following is the status of DMARC adoption among the 713 US government email domains we surveyed:
- 14% have no DMARC record.
- 5% have a record at the p=none monitoring phase.
- 14% do not follow best practices, leaving domains exposed or without visibility.
- 5% have a DMARC policy of p=quarantine, the penultimate policy progression before p=reject.
- 62% are at p=reject and take full advantage of the protection DMARC offers.
DMARC Policy Compliance: Baseline Steps and Common Errors
In addition to capturing the DMARC adoption data as we ran domains through our DMARC Management Platform, we also discovered problem areas for the people deploying DMARC for the .gov domains.
We found that sixty percent of the domains involve SPF errors; issues like missing or invalid SPF records, too many DNS lookups and multiple SPF records are commonplace.
Review these guidelines to to help publish accurate, secure SPF records.
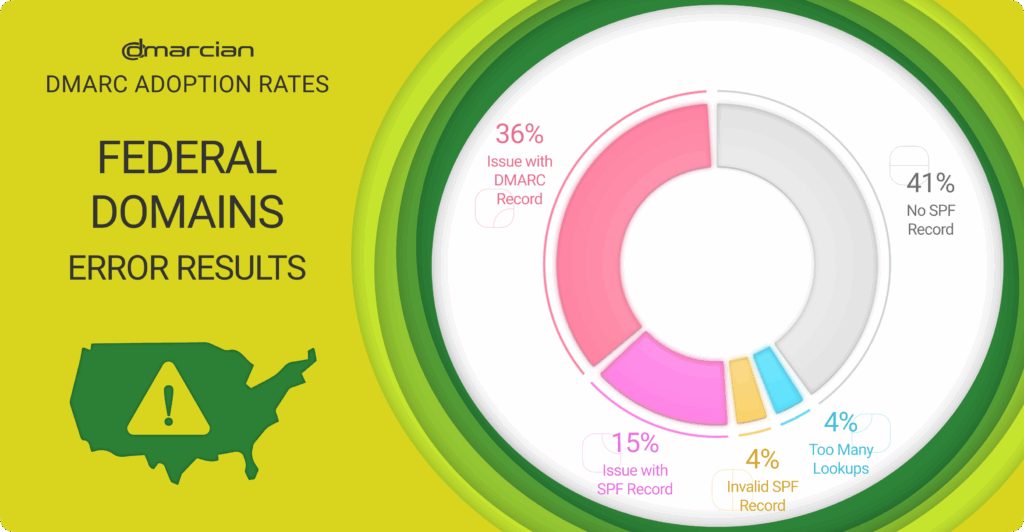
The lack of the required RUA reporting address is also a common error among the US government domains. RUA reports provide an aggregate view of all of a domain’s traffic; without it, DMARC reports aren’t being delivered or leveraged to gain visibility into who and what is descending on behalf of a domain. RUA reports also contain the authentication status for SPF, DKIM and DMARC. Following are the detailed errors from the 108 domains with problematic records:
- 41% have no SPF record
- 36% have a problem with DMARC records
- 15% have an SPF record issue
- 4% have an invalid SPF record
- 4% have the often-sweated too many lookups error
The numbers reveal that the US government has seen progress in protecting their domains with the majority of them achieving p=reject. Gaps, however, remain in the misconfigured SPF, DKIM and DMARC records and progressing DMARC policies to provide full protection from phishing exploits and domain spoofing as specified in CISA directives and broader domain security recommendations.
Although BOD 25-01 only requires action by Federal Civilian Executive Branch agencies, CISA strongly recommends all stakeholders implement these policies. Doing so will reduce significant risk and enhance collective resilience across the cybersecurity community. —CISA
As email industry standards and requirements continue to play a role in influencing non-government organizations, DMARC must be considered as a cybersecurity essential to stop data breaches and ensure emails are delivered in the first place. From government agencies to federal contractors and any business that depends on email, aligning your security practices with public and private guidance will help safeguard your domain and your reputation from email fraud, the most persistent threat out there.
We’re Here to Help
With a team of email security experts and a mission of making email and the internet more trustworthy through domain security, dmarcian is here to help assess an organization’s domain catalog and implement and manage DMARC for the long haul.
Want to continue the conversation? Head over to the dmarcian Forum.


