
Cisco CES DMARC reporting configuration
One of the outstanding features of DMARC is the feedback you get related to email sent from any source using your domain as the RFC5322 identity (friendly from). However, this is contingent on the receiver’s email security provider having the ability to perform DMARC verification on inbound email as well as sending the result of those checks in the form of an aggregate report. One such solution is Cisco’s Cloud Email Security (CES).
When DMARC authentication for inbound email is enabled, the CES appliance can be configured to send DMARC aggregate reports containing the results of those inbound checks. This data is critical for domain owners relative to their DMARC deployment efforts.
These reports are helpful, but more helpful yet is to know who is sending these reports. Knowing the source of the reports is beneficial if you need to follow up with them; better yet, you can easily identify when you send an inbound email to yourself that spoofs your own domain.
With CES, the default reporting identity will be sent from a generic string that looks something like this:
hc1234-56.iphmx.com
As a CES subscriber, you may recognize this as your own MX records. To others, especially the non-CES initiated, this means very little. The good news is that you can change this setting to be recognizable.
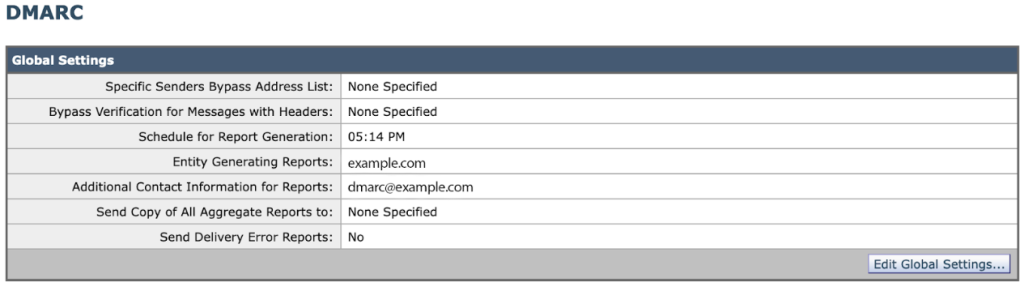
Within your CES admin portal, perform the following:
- Mail Policies -> DMARC
- Click on Edit Global Settings.
- Provide a name for the “Entity Generating Reports” settings. Enter a valid domain name of your organization as a value.
- Submit your changes.
This simple change can also have a useful effect when using a platform like dmarcian’s. Filtering based on your unique reporter can give you a useful inbound view of emails being sent spoofing your domain, legitimately or otherwise.
This simple filter can help identify inbound-only sources that need to be made DMARC compliant and inbound threats you may wish to review and ensure are being blocked, especially before advancing DMARC policy enforcement.
Click here for more information on our Detail Viewer.
We’re Here to Help
With a team of email security experts and a mission of making email and the internet more trustworthy through domain security, dmarcian is here to help assess an organization’s domain catalog and implement and manage DMARC for the long haul.
Want to continue the conversation? Head over to the dmarcian Forum.


