
Spear Phishing in Europe: Why DMARC Matters
What is spear phishing?
Spear phishing is a highly targeted form of phishing in which attackers send convincing, personalised emails to specific individuals or organisations. Unlike generic phishing, these messages are crafted using real information, such as names, job titles or supplier details to appear authentic and trustworthy.
What makes spear phishing particularly dangerous is its high level of seeming authenticity. Attackers often use information from social media or previous data breaches to make messages appear legitimate.
Spear phishing is not just a nuisance; it has real financial and reputational costs. Successful spear phishing attacks can lead to substantial economic losses, data breaches, regulatory penalties and reputational damage. According to the Anti-Phishing Working Group (APWG), Europe recorded over one million phishing attacks in Q2 2025, up 13% from the previous quarter—the highest level since 2023.
European Spear Phishing Risks
Across Europe, spear phishing continues to exploit trusted relationships between businesses, suppliers and public bodies. The European Union Agency for Cybersecurity (ENISA) lists phishing and social engineering as the most common methods attackers use to gain initial network access.
Notable European phishing incidents:
- Marks & Spencer (UK, 2025) – Attackers compromised a third-party contractor and impersonated internal IT staff, leading to a ransomware incident that disrupted operations. The case illustrates how supply-chain impersonation can lead to significant breaches. (Source: Cybernews, May 2025)
- European Defence Sector (2025) – A campaign known as “Laundry Bear” targeted officials across Europe’s defence ecosystem using tailored phishing lures for credential theft and espionage. (Source: CERT-EU Cyber Brief 25-06)
- Political Institutions (Germany and EU, 2024) – State-linked attackers used spear-phishing tactics to compromise political parties and ministries, underlining the threat to democratic institutions. (Source: ENISA Threat Landscape 2024)
These incidents illustrate that spear phishing is not confined to any one sector—it affects finance, retail, healthcare, government and technology alike.
How Spear Phishing Works
- Impersonation: Attackers mimic known identities, such as internal staff executives or vendors.
- Personalisation: Public or leaked information makes the email believable.
- Urgency: Messages often demand immediate action, e.g., a payment change or file approval.
- Exploitation: Clicking on links or opening attachments grants attackers control or access to sensitive credentials.
Even a single successful attempt can compromise entire systems or trigger data breaches.
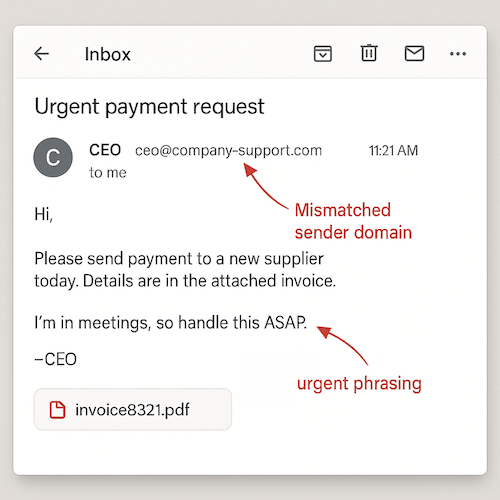
Here’s an example of spear phishing. An employee in the finance department receives an email seemingly from the company’s CEO:
European Compliance and Risk Management
Under European regulation, preventing spear phishing is not just best practice, it’s part of organisational due diligence.
- GDPR (Article 32): Requires “appropriate technical and organisational measures” to protect data. A successful phishing-led breach may constitute a violation.
- NIS2 Directive: Obligates “essential and important entities” to implement effective cybersecurity risk management, including email authentication and incident reporting.
- ISO 27001 / SOC 2: Expect safeguards against social-engineering threats.
- PCI DSS v4.0: Emphasises secure data transmission, which email authentication directly supports.
By integrating phishing defence into compliance frameworks, organisations protect both their customers and their reputation.
How DMARC Helps
Implementing DMARC helps prevent a key attack method—domain impersonation—used in spear phishing. Given the high cost of breaches and the significant role spear-phishing plays in them, investing in strong email authentication, including DMARC, is a wise, forward-looking choice.
Managing spear phishing risks is crucial for demonstrating due diligence across various compliance frameworks. Many data protection and cybersecurity standards mandate organisations to implement measures to prevent unauthorised access or breaches. As spear phishing is a prevalent attack technique, overlooking it can lead to compliance issues.
Here’s how DMARC protects you:
- Authentication: DMARC builds on SPF and DKIM to verify that emails truly originate from authorised servers.
- Visibility: It provides reports showing who is sending on behalf of your domain, including unauthorised sources.
- Enforcement: Organisations can instruct mail servers to reject or quarantine unauthenticated messages, blocking impersonation before it reaches inboxes.
- Compliance Support: Demonstrating active DMARC enforcement aligns with GDPR Article 32 and NIS2 obligations to maintain appropriate controls.
In short, DMARC prevents others from impersonating you, strengthening both brand trust and regulatory compliance.
Spear phishing is among Europe’s most persistent cyber threats, blending deception, impersonation and human psychology. Defending against it requires a balance of technical controls, staff awareness and regulatory compliance.
DMARC provides a foundation for that defence: it verifies identity, protects trust, and supports compliance obligations under regulations such as GDPR and NIS2.
In today’s European threat landscape, authenticating your email is no longer optional—it’s essential.
We’re Here to Help
With a team of email security experts and a mission of making email and the internet more trustworthy through domain security, dmarcian is here to help assess an organization’s domain catalog and implement and manage DMARC for the long haul.
Want to continue the conversation? Head over to the dmarcian Forum.


