DMARC Status of Top Fast Food Restaurants
When we read the news of McDonald’s data breach, it brought to mind the history of quick-serve joints being targeted and infiltrated. Zaxby’s 2013 Point of Sale (POS) breach, Dunkin’s 2018 credentials leak, and Chipotle’s 2021 email compromise illustrate how these restaurants are in the crosshairs of criminals who spend their days attempting to penetrate poorly protected IT networks.
Based on what we’ve read, the recent McBreach was small in scope and didn’t expose sensitive data, but it could have been much worse. “Why are fast food chains being targeted,” you may wonder. Traditionally, financial institutions have been seen as the prime target for cyber attacks, given the conveyance of large sums of money, the availability of personal information, and the time-is-of-the-essence nature of their business. However, these institutions have typically been much more proactive in deploying cyberdefense measures, causing criminals to look for other opportunities in verticals that may not be as well defended.
Given our research, we discovered that the majority of top fast food domains aren’t protected, so they’re fair game for cybercriminal phishing to gain network access. In addition to unprotected domains, imagine the wellspring of credit and debit card data these restaurants manage via POS devices.
Combine these two factors—weak network protection and financial credentials—and cagey cybercriminals have an opportunity to gain entrée to the network to access stored data or worm into the connected POS terminal to take the data flowing through it. They can access the POS remotely when an attacker gains access by landing a phish or via another attack vector. Often, when these bad actors steal credit card numbers and credentials, they sell cloned versions on the dark web. Unsuspecting card holders are in the dark until illegitimate charges start appearing on their statements.
From the perspective of the fast-food chain, their brand is tarnished by these breaches and can result in loss of customer trust. Chains also have to fork over data breach clean-up costs, which, according to IBM, have soared to an average of $4.24 million per incident, the highest ever.
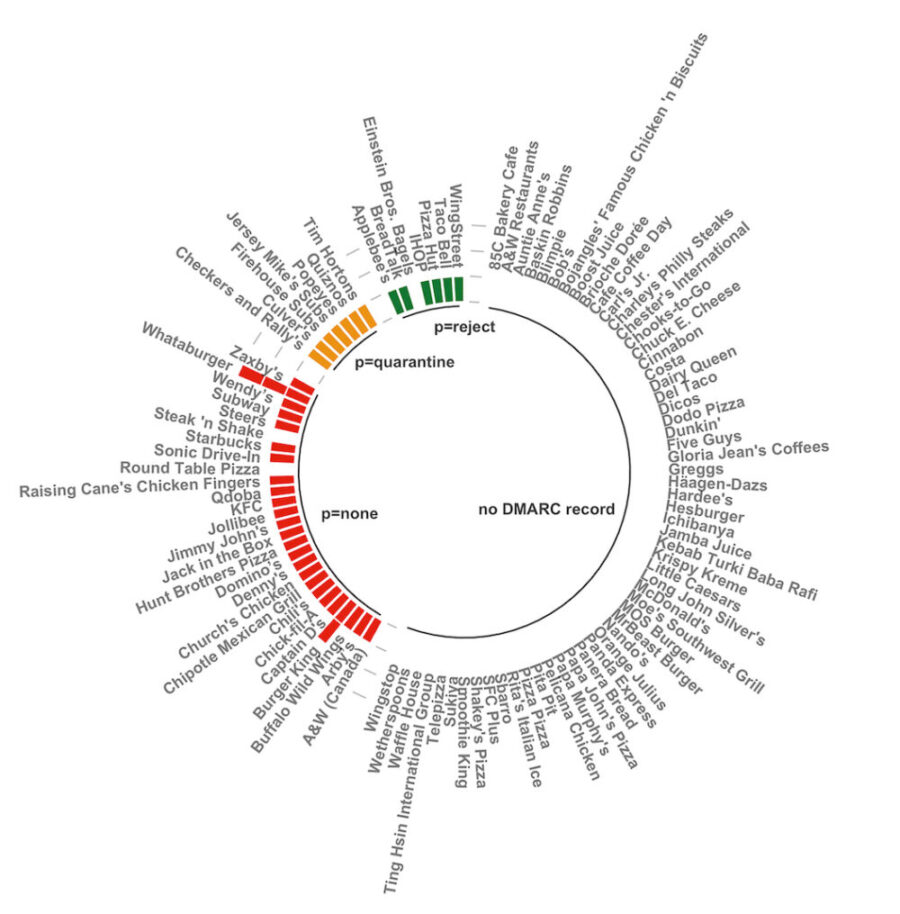
At the time of publishing this research, this is what we discovered with the top 99 fast food chains based on their number of locations around the world:
- ~59% had no DMARC record
- ~27% had a DMARC record with a p=none policy
- ~7% had a DMARC record with a p=reject policy
- ~7% had a DMARC record with a p=quarantine policy
Forty-one percent of these companies have a DMARC record, so they’re aware of the email ecosystem standard, and we can assume that those not at compliance are working to protect their domains with an enforced DMARC policy to stop criminals from using their domains to fool customers and vendors with phishing exploits. Unfortunately, fifty-nine percent lacked a DMARC record; these companies’ domains are not secured from email spoofing and the resulting losses.
Read more dmarcian DMARC adoption research:
- Fortune 100 DMARC Policies
- Top 100 Global Banks DMARC Policies
- Top 100 Canadian Companies DMARC Policies
dmarcian has assisted fast-food restaurants (Pizza Hut, Wing Street, Taco Bell) in achieving DMARC compliance. With a team of security experts and a mission of making email and the internet more trustworthy through domain security, we’re here to help people implement and manage DMARC for the long haul.
Give our DMARC Management Platform a complimentary test run; our onboarding and support team will help you along the way.
Want to continue the conversation? Head over to the dmarcian Forum.


