
Single Sign-On Support for Enterprise
Our Single Sign-On (SSO) support leverages Security Assertion Markup Language (SAML) version 2 for Enterprise users. This expedites access to your dmarcian account by letting you sign in with your existing corporate credentials, which means one less password to keep track of.
With our SSO, you can easily manage SSO access and user permissions to all of your accounts in dmarcian centrally while adhering to your organization’s security and access policies.
Before getting into the details for SSO configuration, let’s first talk about some basic concepts and terminology:
Authentication
Authentication defines how the user is identified in a system—usually through a login process. Traditionally, a user registers for an account providing authentication credentials (username and password) and uses them to log in moving forward.
In the past, this has been sufficient, but it does have limitations. For example, what happens if you have a several employees at your company that you want to grant access to dmarcian? Previously, the only option was to add the employees as new users to your account—each with their own credentials. It is inconvenient for users to remember yet another complicated password, so they tend to use the same password for many registrations in different applications, which increases the chance of having accounts hacked if one authentication is discovered.
Federated Identity
Federated identity helps in solving the problem with users having different credentials for the applications they use in your company. Instead of letting each application store user credentials, companies can use a central identity infrastructure (Identity Provider or IdP) and allow third parties to securely authenticate users. This is what led to the birth of federated protocols such as Secure Assertion Markup Language (SAML).
Here are some common terms that we will use in this how-to:
- A Service Provider (SP) is the entity providing the service – dmarcian.
- An Identity Provider (IdP) is the entity providing identities – we will use Okta for an IdP in this how-to but the process is similar to any other available option that supports SAML.
- A SAML Request (also known as an authentication request) is what dmarcian sends to the IdP when a user wants to log into dmarcian.
- A SAML Response is generated by the IdP on successful user authentication. It contains information related to the authenticated user, like email for example. This response is sent to dmarcian notifying us who the authenticated user is so access can be granted.
With all the basics laid down we can get our hands dirty – let’s configure SSO!
How to Configure SSO
We will use Okta as an Identity Provider in this how-to, but the steps should be similar for any other IdP. Configuration instructions specific to Microsoft Office 365 (Azure AD) can be found here.
Step 1 – add dmarcian to your IdP
- Login to dmarcian, navigate to your User Profile in the upper right-hand corner and select “Preferences.”
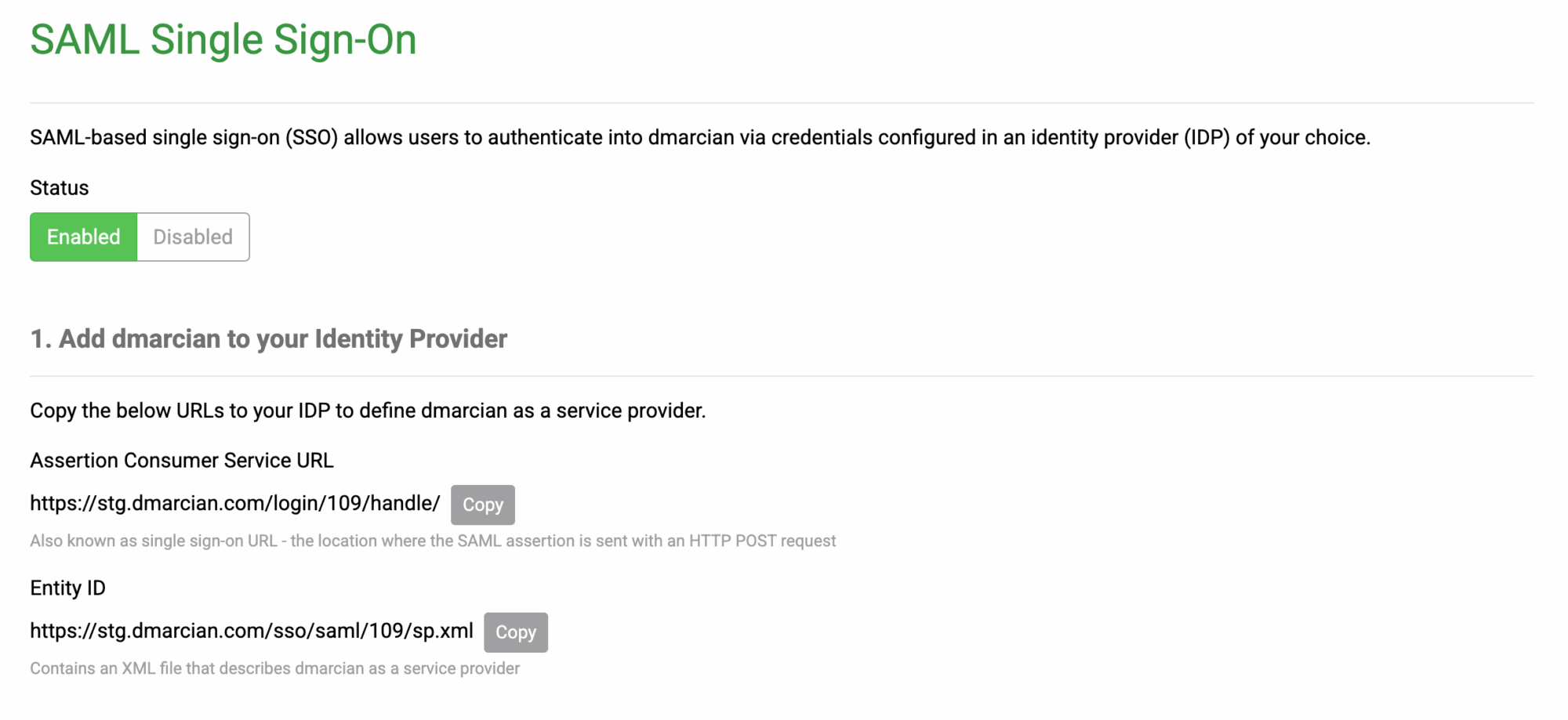
- You will see the new SAML Single Sign-On configuration page where SSO will be disabled by default – enable it.

- Leave the SSO configuration page open since you will have to copy some information from it while adding dmarcian as a Service Provider to Okta.
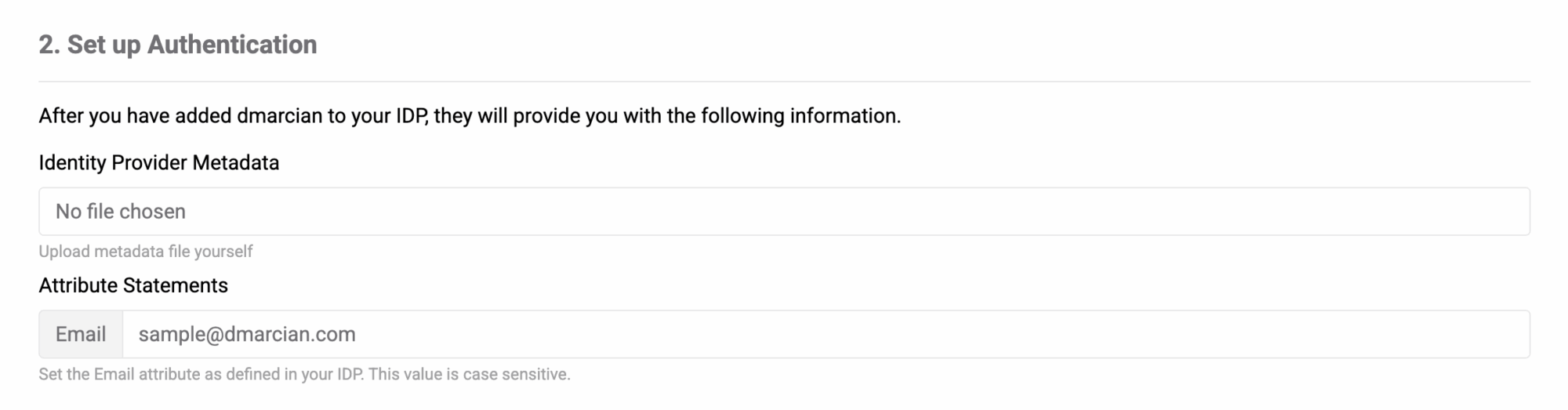
- Follow this official guide to add dmarcian to Okta with the following key notes:
On step 8 – paste the Assertion Consumer Service URL as the Single sign on URL and the Entity ID as the Audience URI (SP Entity ID).
On step 9 – do not forget to add at least the user email as an attribute statement and be sure to save the name you have provided – we will need it later when configuring SSO at dmarcian.
On step 11 – download the Identity Provider metadata file and save it – we will need it too.
Step 2 – set up authentication at dmarcian, modify login URL
Great! Now that you have configured Okta to recognize dmarcian as an SP we can configure the authentication process at dmarcian. We’re almost there – just follow the next steps.
- Get back to the SAML Single Sign-On configuration page at dmarcian (we’ve left it open in the previous steps).
- Upload the IdP metadata file directly. Also make sure to fill in the email attribute statement name you’ve set up at Okta.
- Modify the login URL that users from your company will use to log into dmarcian (optional – we provide some default value if you do not care how the URL looks like).
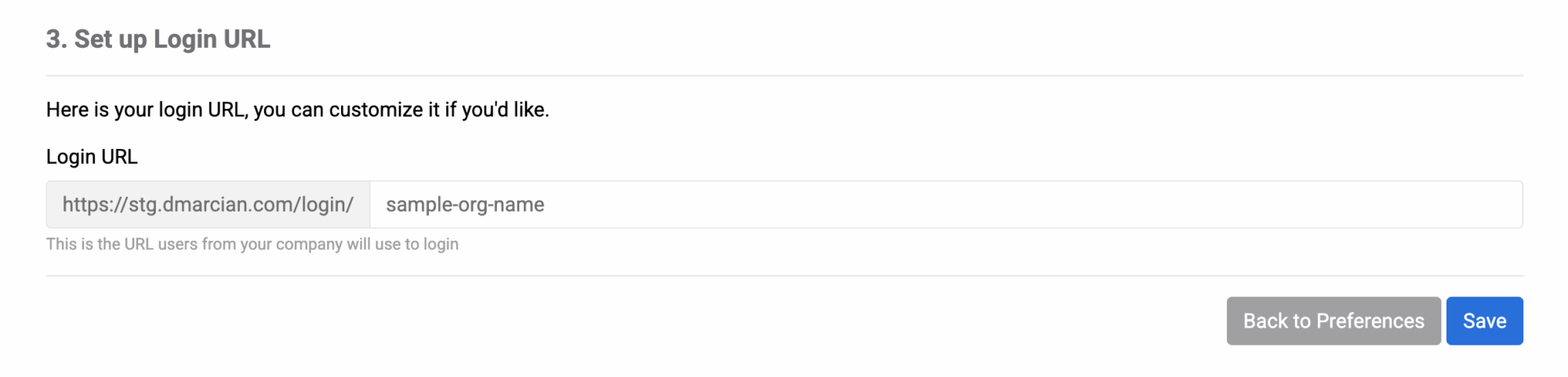
- Click Save. If there are no errors, your SSO configuration is complete!
- Optional Configuration: Require SSO for all users. By default, the account owners and administrators are permitted to login with their username and password, even with SSO enabled. Enabling this option will require SSO login for all users.
Step 3 – add users, configure access control, notify users of login URL
Although the authentication process is now configured you have to add the users that are allowed to log into dmarcian through your IdP. This is a strict policy we have decided to follow so you have full control over which users exactly can use the application.
Navigate to Manage Settings -> User Management to organize your user list.
Navigate to Manage Settings -> Access Control to configure what each user can do at dmarcian.
Congratulations!
You have successfully configured Single Sign-On!
Setting up dmarcian SSO with Microsoft Office 365 (Azure AD)
Our SSO is available as an app in Azure’s Marketplace and you can set it up directly from here.
Note: the tutorial describes the overall integration of the app and includes URLs to all regions — be sure to use the appropriate instance URL in your setup.
Want to continue the conversation? Head over to the dmarcian Forum


