
Subdomain Abuse Goes Mainstream
Last week, LinkedIn was the target of a massive, global cyber attack.
The attack came in the form of phishing that looks almost exactly like real LinkedIn address confirmation emails.
Only two things differed:
- The email was sent from spoofed sub-domains.
- The “Click Here” link of the HTML version of the email lead to a malicious site.
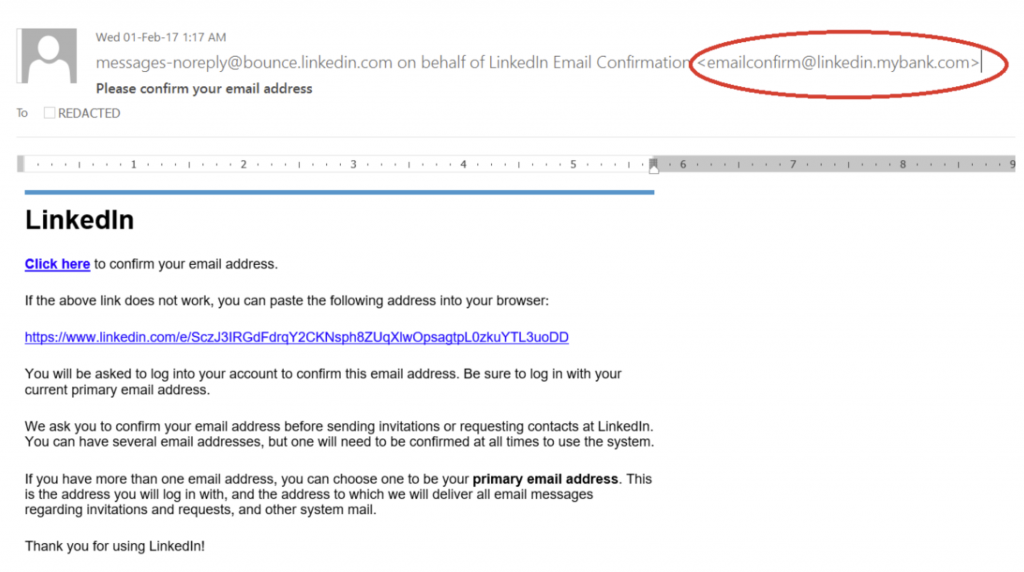
The cybersecurity attack works when people follow the “click here” link and find themselves with malware on their computer and stolen LinkedIn credentials. In no way is LinkedIn’s real website involved in this attack: the attack relies on people assuming that the email is real.
This type of email spoofing happens all the time. What makes this particular attack special is in its breadth. Last week, a huge number of dmarcian users saw abuse of the form linkedin.example.org (where example.org belonged to the dmarcian user). A second wave of abuse gave us the form of linkedin-sub.example.org, where sub.example.org was likely to be a real sub-domain.
Before last week, dmarcian users would rarely see large numbers of fake sub-domains. When it did happen, we’d work with the user to roll out policies to block the abuse. Last week, more than 42% of all dmarcian client accounts saw this attack, spanning more than 10,000 unique spoofed domains from more than 3,000 hosts around the globe. The breadth of this type abuse is new and leads us to declare that sub-domain abuse has now gone mainstream.
Disallow Fake Subdomains with DMARC
DMARC has the ability to disallow the use of fake sub-domains. Now that sub-domain abuse is set to become the norm, we are making changes to dmarcian to make sub-domain protection available to more people earlier in the deployment process.
Changes will guide dmarcian users to:
- Publish explicit DMARC records for all legitimate sub-domains.
- Use DMARC’s sub-domain policy tag to disallow use of all sub-domains that do not have an explicit DMARC record.This would look like:
PARENT DOMAIN DMARC record: v=DMARC1; p=none; sp=reject; rua=...
SUB DOMAIN DMARC record: v=DMARC1; p=none; rua=...
Sub-domain DMARC records do not need to use the sp= tag due to the way DMARC record discovery works.
The above approach allows domain owners to work through DMARC compliance at their own pace while disallowing the use of fake sub-domains (like the LinkedIn abuse above).
We are rolling out a DMARC program to help customers protect themselves from this style of sub-domain abuse. This immediate form of protection can be implemented aggressively at the front end of DMARC deployment. Contact us for more information on preventing sub-domain abuse on your domain.


