Phishing and Social Engineering Loom Large in Verizon 2021 Data Breach Investigation Report
If you haven’t read it yet, Verizon has released its clever, compelling 2021 Data Breach Investigations Report. We thought we’d take a look at the report’s investigation of phishing, which has been on the rise during the pandemic and is mentioned over 50 times in the report.
Phishing remains one of the top Action varieties in breaches and has done so for the past two years. Not content to rest on its scaly laurels, however, it has utilized quarantine to pump up its frequency to being present in 36% of breaches (up from 25% last year). This increase correlates with our expectations given the initial rush in phishing and COVID-19-related phishing lures as the worldwide stay-at-home orders went into effect.
Verizon 2021 Data Breach Investigations Report
Verizon researchers discovered 29,207 security incidents from 88 countries; 5,258 of those were confirmed as data breaches. Here are the nitty gritty numbers on the data breaches:
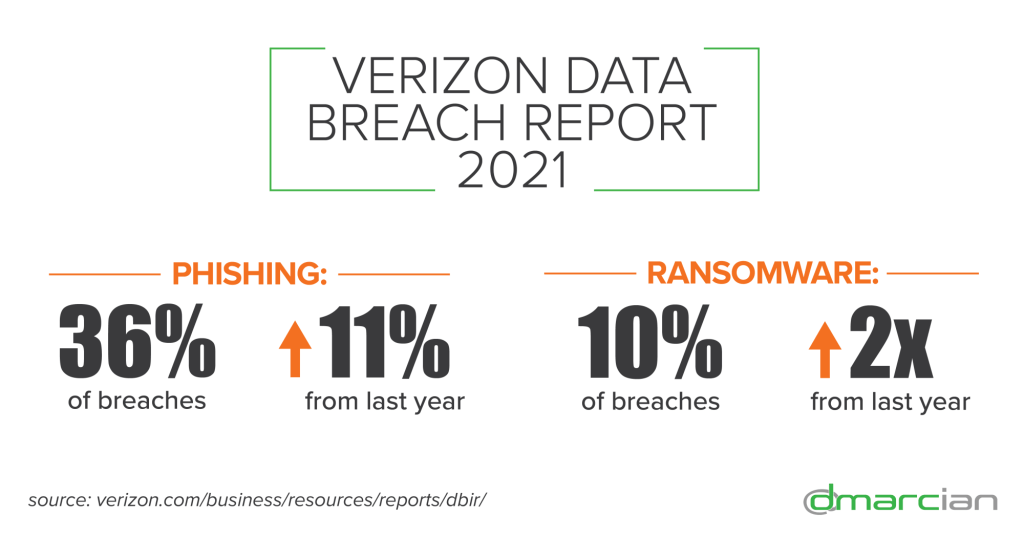
- Phishing was present in 36% of breaches—up 11% from last year
- Ransomware appears in 10% of breaches—more than double from last year
- 85% of breaches involved a human element
- 61% of breaches involved credential data
Phishing followed by Phone Call
In the Global Cyber Alliance’s Cyber Trends 2021 event, Phillip Larbey, Verizon’s Managing Principal, Investigative Response & Threat Intelligence, presented data from the report and provided context and insight. One of these dealt with the trend of a phishing campaign followed by a phone call. On the fraudulent call, the phisher urged the email recipient open the email. Given the immediacy and pressure of another person asking them to click on the phishy email in real time, very often the victim would click; as a result, the pernicious payload was released on the network. This wire fraud tactic ushers in a new flavor of spear phishing exploit that integrates a targeted, socially engineered email AND phone call.
Business Email Compromise
In the social engineering section of the 2021 Data Breach Investigation Report, Verizon says “phishing is responsible for the vast majority of breaches in this pattern, with cloud-based email servers being a target of choice. Business Email Compromises (BECs) were the second most common form of Social Engineering. This attack scenario reflects the meteoric rise of Misrepresentation, which was 15 times higher than last year in Social incidents.” 58% of the attacks researched in the report that were successful in misdirecting funds, the average “loss was $30,000 with 95% of BECs costing between $250 and $984,855.”
Credential Theft = Big Payout
Credential theft via social engineering and phishing continues to be a high priority for cyber criminals. “Credentials are the glazed donut of data types,” Verizon says. With this hijacked email, network, and application login information, threat actors can further infiltrate networks and systems to execute BEC tactics, install malware and ransomware, steal personally identifiable information, and plunder intellectual property and confidential information.
“Given the prevalence of the Phishing attacks, this is where the credentials frequently come into play,” the report states. “Personal data is a prime target as well, since that includes such data elements as Social Security/Insurance numbers paired with other bits of information that allow criminals to commit further financial fraud.”
Public Administration in the Crosshairs
The Public Administration sector is squarely in the crosshairs of phishers. “Actors who can craft a credible phishing email are absconding with Credentials at an alarming rate in this sector,” according to Verizon. “The Social Engineering pattern was responsible for over 69% of breaches in this vertical. Clearly, this industry is a favorite honey hole among the phishing fiends. The Social actions were almost exclusively Phishing with email as the vector. Pretexting was rarely leveraged at all, and why should they go to all the work of inventing a scenario when a straight up phish gets the job done?”
Utilities Fall for Social Engineering
And we would be remiss if we didn’t talk about the utility sector for a minute. Verizon’s research category where utilities lie also includes mining, quarrying, and oil & gas extraction. Social engineering is again prominent “with sustained phishing campaigns occurring against some organizations. Social Engineering accounts for 86% of the breaches in this vertical, followed by System Intrusions and Basic Web Application Attacks.” As of the publication of this summary, details on how the atrocious Colonial Pipeline attack hadn’t surfaced; given the report statistics, one has to wonder about social engineering and phishing attack vectors.
How DMARC and dmarcian Can Help
DMARC comes into play by helping to protect internet domains from criminals using socially engineering and phishing attacks. DMARC ends up being the glue that lets organizations manage email as a domain-based service. DMARC’s utility as an anti-spoofing technology stems from a far more significant innovation; instead of attempting to filter out malicious email, why not provide operators with a way to easily identify legitimate email? In effect, DMARC’s promise is to augment the “filter out bad” email security model with a “filter in good” model.
dmarcian’s mission is to see universal DMARC adoption. We advocate for the technology and advance it by helping organizations of all shapes and sizes deploy it. We’ve learned that a properly structured DMARC deployment can lay the foundation for an organization’s trustworthy online presence.
We’re here to help assess an organization’s domain catalog and implement and manage DMARC for the long haul. You can register for a free trial where our onboarding and support team will help you along the way.
Want to continue the conversation? Head over to the dmarcian Forum.


