
Verizon Data Breach Investigations Report: Social Engineering Insights
In the 17th edition of the Data Breach Investigations Report (DBIR), Verizon researchers and their partners analyzed 30,458 security incidents that took place between November 1, 2022, and October 31, 2023. 10,626 of the incidents were confirmed data breaches with victims in 94 countries. The report discusses the evolving nature of cyber threats, the persistent challenge of human error, and the importance of vulnerability management to mitigate risks.
Our ways-in analysis witnessed a substantial growth of attacks involving the exploitation of vulnerabilities as the critical path to initiate a breach when compared to previous years. It almost tripled (180% increase) from last year, which will come as no surprise to anyone who has been following the effect of MOVEit and similar zero-day vulnerabilities.
Verizon 2024 Data Breach Investigations Report
2024 Takeaways
- 68% of breaches involved a non-malicious human element, like a person falling victim to a social engineering attack or making an error
- 62% of financially motivated incidents involved ransomware or extortion, with a median loss of $46,000 per breach
- 15% of breaches involved a third party or supplier, such as software supply chains, hosting partner infrastructures or data custodians
- 14% of breaches involved the exploitation of vulnerabilities as an initial access step, almost triple the amount from last year’s report
Social Engineering
DBIR researchers find that “pretexting continues to be the leading cause of cybersecurity incidents, with actors targeting users with existing email chains and context.” Because of the extensive MOVEit event, extortion also grew dramatically. With a boost from bad actors leveraging AI, it’s no surprise that phishing and pretexting by email accounted for 73% of incidents in the social engineering sector. Following are the DBIR social engineering numbers:
- 3,661 incidents with 3,032 confirmed instances of data disclosure
- Threat actors’ motives were overwhelmingly financial at 95% and espionage at 5%.
- Types of compromised data included credentials (50%), personal (41%), internal (14%) and other (14%).
Top Action vectors in Social Engineering breaches
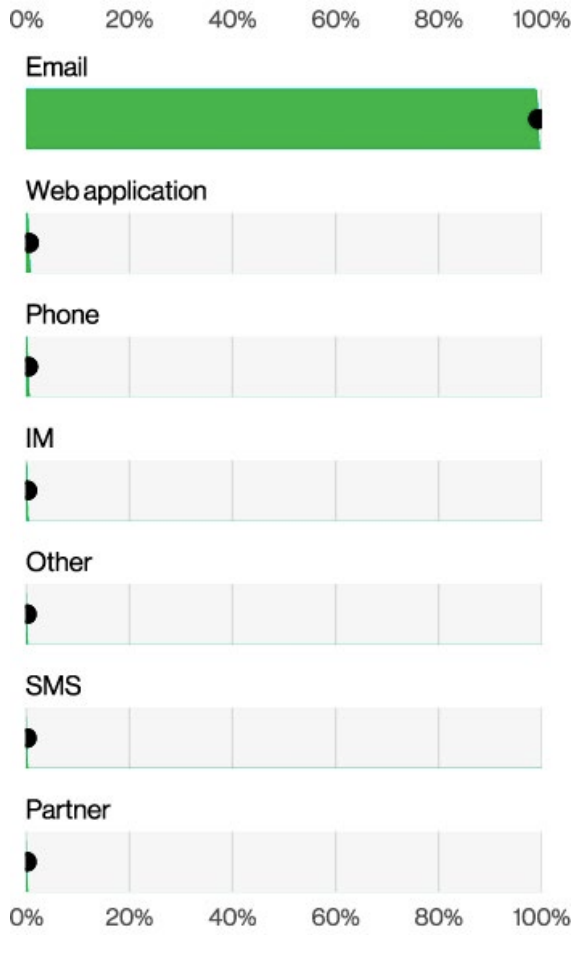
We tend to see the core social tactics such as Pretexting and Phishing still being used often. Other tried-and-true tactics such as attacks coming in via email, text and websites aren’t necessarily the most exciting, but any security professionals who have been around for any length of time have probably seen these contenders in some capacity over their careers — Verizon 2024 Data Breach Investigations Report
DBIR authors write that though pretexting has plateaued since last year, it remains as the top social engineering incident. They consider pretexting “as a stand-in for BEC, where attackers leverage existing email chains to convince victims to do something, such as update an associated bank account with a deposit.” BEC continues to affect organizational bottom lines with the numbers holding steady from last year with the “median transaction hovering around $50,000.”
Phishing—Ransomware’s Gateway
DBIR researchers also report that “social attacks, such as those involving phishing, have long played their part in ushering in a ransomware deployment, as typified by the leveraging of those techniques in the ALPHV breach of MGM Resorts and other entertainment groups.”
Because phishing is a leading attack vector for gaining access to a network and installing ransomware, CISA recommends enacting SPF, DKIM and DMARC to help prevent domain spoofing and network intrusion. A foundational protection against ransomware, DMARC allows domain owners to protect their domains from unauthorized use by fighting ransomware’s attempted delivery by email.
The first lesson to learn is that Phishing attacks happen fast. The median time to click on a malicious link after the email is opened is 21 seconds, and then it takes only another 28 seconds to enter the data. That leads to a frightening finding: The median time for users to fall for phishing emails is less than 60 seconds.
Verizon 2024 Data Breach Investigations Report
Phishing continues to be a prevailing method of attack to gain access to organizational networks. The rapid click-through and data entry times for phishing emails highlight the urgency for organizations to implement phishing prevention controls like DMARC alongside regular and comprehensive user training. Luckily, the authors report an increase in phishing awareness by end users. In simulated phishing exercises, 20% of users reported phishing emails without clicking on them, and 11% reported the email after clicking the link, which translates into growing awareness and responsiveness when people are faced with phishing attempts.
Read more about how DMARC allows people to protect their domains by fighting ransomware’s delivery by email.
How DMARC and dmarcian can help
DMARC comes into play by helping to protect internet domains from criminals using social engineering and phishing attacks. It ends up being the glue that lets organizations manage email as a domain-based service. DMARC’s utility as an anti-spoofing technology stems from a far more significant innovation; instead of attempting to filter out malicious email, why not provide operators with a way to easily identify legitimate email? In effect, DMARC’s promise is to augment the “filter out bad” email security model with a “filter in good” model.
dmarcian’s mission is to see universal DMARC adoption. We advocate for the technology and advance it by helping organizations of all shapes and sizes deploy it. We’ve learned that a properly structured DMARC deployment can lay the foundation for an organization’s trustworthy online presence.
We’re here to help you assess your domain catalog and implement and manage DMARC for the long haul. You can register for a 30-day trial where our onboarding and support team will help you along the way.
Want to continue the conversation? Head over to the dmarcian Forum.


