
Hosting Dynamic MTA-STS Policies for Multiple Domains with Cloudflare Workers
We’ve had a recent trend of customers asking us how to set up MTA-STS policies and created a guide to provide assistance.
This guide walks you through publishing MTA-STS (Mail Transfer Agent Strict Transport Security) policies for multiple domains using a single Cloudflare Worker. With this approach, you can serve the appropriate policy based on the domain being queried, eliminating the need for a separate file or web server per domain.
Cloudflare MTA-STS prerequisites
Before we get started, make sure you meet these necessities:
- Your domains must be managed through Cloudflare.
- You need full access to your Cloudflare dashboard.
Step-by-Step MTA-STS Instructions
1. Access Cloudflare Workers
2. Create a New Worker
3. Replace the Default Code
Replace the default code with the following—this Worker dynamically returns an MTA-STS policy file based on the domain from which the request originates:
export default {
async fetch(request, env, ctx) {
const hostname = new URL(request.url).hostname;
// Define policies per domain
const policies = {
"mta-sts.domain.org": `version: STSv1
mode: testing
mx: mail.domain.org
max_age: 86400`,
"mta-sts.example.org": `version: STSv1
mode: enforce
mx: mail.example.org
max_age: 86400`
};
const policy = policies[hostname];
if (policy) {
return new Response(policy, {
headers: { "Content-Type": "text/plain" }
});
} else {
return new Response("404 Not Found", {
status: 404,
headers: { "Content-Type": "text/plain" }
});
}
}
}Note: Update the policy content for each domain to match your MX records and desired enforcement mode (testing, enforce or none).
4. Deploy the Worker
- Select “Deploy” to save changes and publish your Worker.
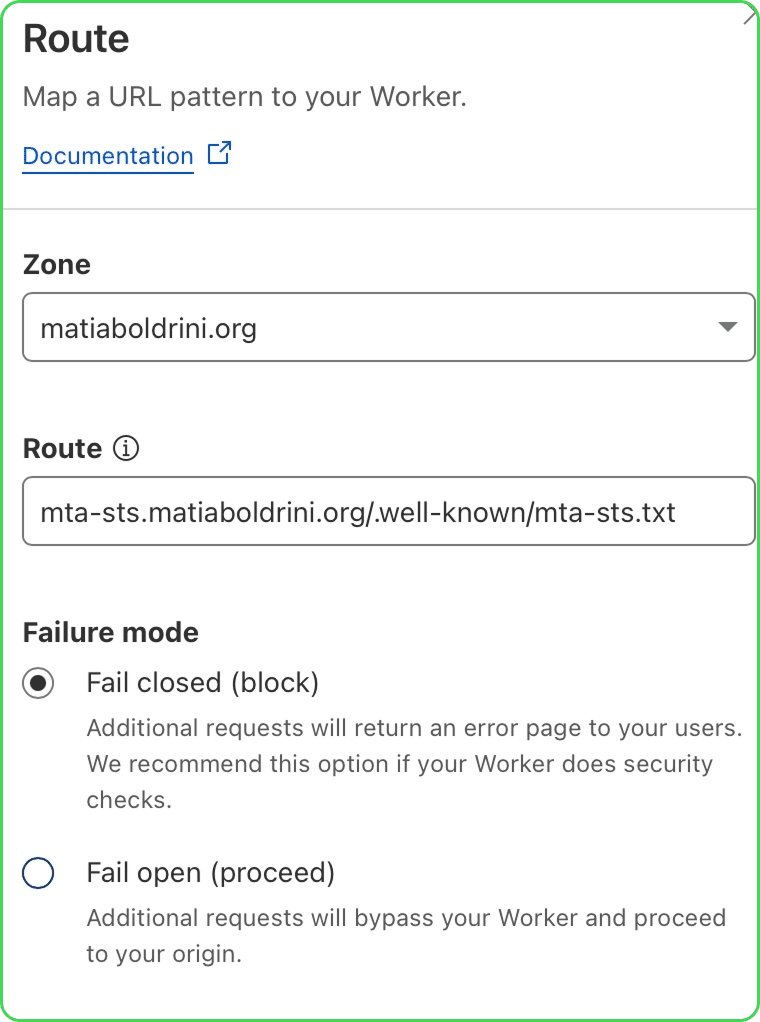
5. Configure route(s) per domain
In the Worker dashboard complete the following:
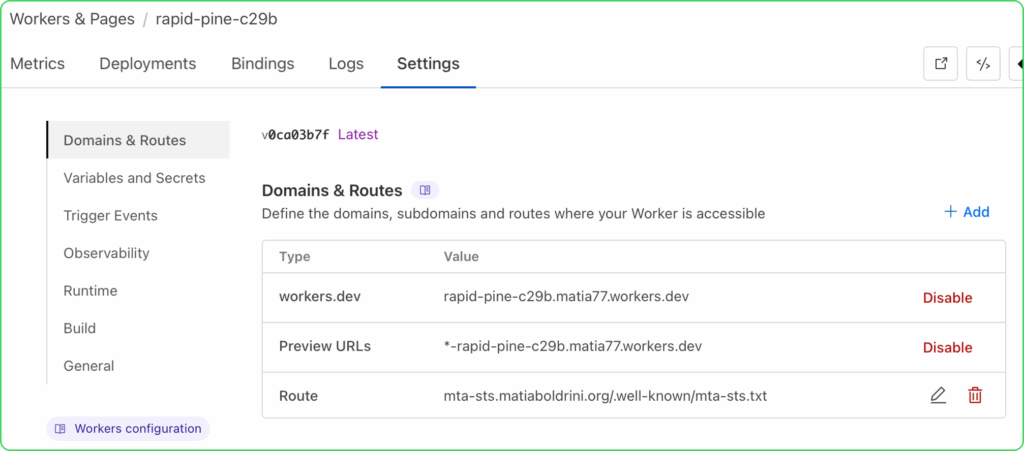
- Go to the Settings tab
- Under “Domains & Routes,” click “Add” to create a route for each domain. Here’s an example:
Domain
example.com
example.org
Route
mta-sts.example.com/.well-known/mta-sts.txt
mta-sts.example.org/.well-known/mta-sts.txt
6. Set Up DNS Records
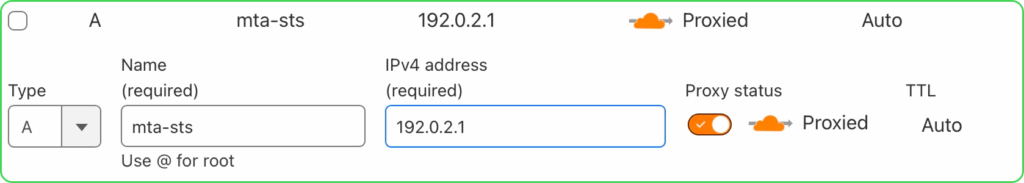
6.1 In each domain’s DNS settings, create an A record for the mta-sts subdomain:
- Type: A
- Name: mta-sts
- Value: 192.0.2.1 (placeholder IP)
- Proxy status: Proxied (orange cloud)
- Repeat for each domain
6.2 Ensure to publish an MTA-STS text record as well:
- Type: TXT
- Name: _mta-sts
- Value: “v=STSv1; id=20250630v01;”
- Note: the “id” string can be anything. We recommend using a format that includes the date and version of when the record was created.
7. Test Your Setup
Once DNS has propagated, test your MTA-STS policy file:
- Access it directly: https://mta-sts.yourdomain.com/.well-known/mta-sts.txt
- Alternatively, you can use dmarcian’s MTA-STS inspector tool: https://eu.dmarcian.com/tls-inspector/?domain=yourdomain.com
Starting on July 3, 2025, Cloudflare began requiring SPF or DKIM authentication to forward emails and recommends that all senders implement DMARC.
dmarcian is here to help
With a team of email security experts and a mission of making email and the internet more trustworthy through domain security, dmarcian is here to help assess an organization’s domain catalog in light of the upcoming DMARC updates. We can help you implement and manage DMARC for the long haul.
Want to continue the conversation? Head over to the dmarcian Forum.


