
Securing Your Supply Chain from Phishing Attacks
In this piece, Tass Kalfoglou, the director of our APAC Business Unit, sheds light on supply chain vulnerabilities and the need to level up domain security.
Phishing and Supply Chains
For many years running, phishing has been the most common and successful cyberattack vector; over 90% of attacks begin with an ill-intended email. When applied to our deeply interconnected business ecosystem, phishing exploits expose supply chain vulnerabilities that can lead to massive disruptions. From invoice fraud to network intrusion, supply chains, too, are only as strong as their weakest link. With supply chain attacks on the rise, it’s critical that organisations in a supply chain have their domains locked down from phishing exploits.
What is a Supply Chain?
A supply chain is a complex, linked network of entities, processes and resources that work together to produce and deliver goods and services. Involving multiple stages, supply chains can include everything from sourcing raw materials, manufacturing, logistics, distribution, final delivery and sales operations.
Supply chains can span across industries such as retail, technology, healthcare and manufacturing, making them an essential component of global commerce.
Securing your supply chain, “the people and companies you do business with,” is critical because your organization’s security is only as strong as its weakest link. If a supplier, vendor or partner is compromised, that risk can extend to you, leading to financial, operational and reputational damage.
When an organisation focuses on maturing its own security posture, it becomes important for them to begin looking to their suppliers and vendors, their supply chain, to ensure they are not introducing external risk.
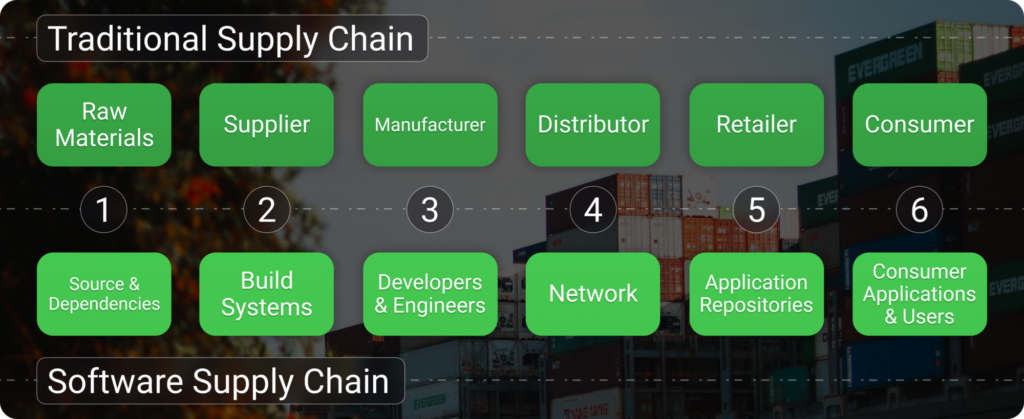
Traditional vs Software Supply Chain
Where the traditional supply chain refers to the movement of physical products from raw materials to finished goods, the software supply chain involves the development, distribution and deployment of software, often using third-party code, open-source libraries and cloud services that are prone to vulnerabilities or injection of malicious code.
It is important to highlight the software supply chain as this is something that may be overlooked by your organisation. When performing a supply chain risk assessment, it is important to consider the software vendors that your organisation uses.
Supply Chain Attack Surface
We’re going to focus on traditional supply chain attacks, where bad actors reach the targeted network by researching and discovering a weakness in a third-party supplier or vendor. They exploit that third-party weak link to gain access to their target’s network and digital assets.
As the number of your suppliers, partners, vendors and interactions grows, the potential entry points for an attack increase. The ability to attack many targets simultaneously makes supply chains an attractive target for criminals.

Supply Chain Attack Gateways
Suppliers
Suppliers provide goods and services to organisations and, like any other third-party vendor, can be an entry point exploit of the companies they serve. An all-too-common tactic is invoice fraud; in this exploit, a supplier’s email is compromised and a threat actor impersonates said supplier, sending a fake invoice that directs payment to a bogus bank account.
In a recent case in the District Court of Western Australia, Mobius Group Pty Ltd v Inoteq Pty Ltd (2024), Mobius’ email was compromised resulting in Inoteq sending funds to a fraudulent bank account. The court ruled that the responsibility fell to Inoteq, requiring them to pay the amount again to Mobius.
Software Vendors
An email service provider (ESP) is a common type of vendor that organisations use to send their customers marketing and transactional emails. If an ESP’s network is breached, threat actors could have access to your customer data or mailing lists. They can use this intel as a basis to launch phishing campaigns against your customers; with escalated privileges, they can send emails directly to your customers posing as you.
Strategic Partners
When a strategic partner has privileged access to systems, data or intellectual property, the attack surface extends into their environment. Threat actors can exploit that trust relationship to launch attacks upstream or downstream. Your managed service provider (MSP) is one example. A breach of your MSP may involve unauthorized access to systems and private information.
You might remember the SolarWInds attack. In that supply chain attack, one of the most pervasive ever, bad actors exploited a software update and gained access to thousands of SolarWinds customers, causing losses in the tens of millions of dollars. Fortinet reported that businesses in Singapore lost 9.1% of their annual revenue because of the SolarWinds supply chain attack.
How Industries Secure Supply Chains
Australia – Defence Industry
The Defence Industry Security Program (DISP) is an Australian Department of Defence initiative that helps defence contractors and their supply chains meet strict security requirements, thereby reducing overall supply chain risk. By setting uniform standards and processes, DISP makes sure that businesses working with the Australian Defence Force (ADF) protect classified or sensitive information, systems and assets.
Payment Card Industry
While PCI DSS (Payment Card Industry Data Security Standard) is not a comprehensive supply chain framework like ISO 28000 or certain defense/industrial programs, it does address key aspects of supply chain risk relevant to handling payment card data. By mandating vendor oversight, formal compliance checks and secure configurations, PCI DSS ensures that everyone in the payment chain—from your internal systems to outsourced providers—maintains consistent, audited security controls that help prevent breaches and reduce supply chain vulnerabilities.
New Zealand – Government
The New Zealand Information Security Manual is the primary security framework issued by the government. It provides guidelines, standards and best practices for managing and securing information systems. While not explicitly using the phrase supply chain, you can find many baseline controls that all point to securing the supply chain of the government. A secure email framework that ensures encrypted email communications of sensitive information and the use of DMARC to mitigate phishing is just one example of securing the supply chain.
DMARC’s Role in Reducing Supply Chain Risk
Email remains the top initial attack vector for cybercriminals because of its ease of manipulation, and securing your catalogue of domains is crucial in reducing your supply chain risk. The primary control to observe and restrict email domain usage is DMARC.
Deploying DMARC and having your supply chain vendors do the same is one way everyone can trust the many email messages flowing among you and your supply chain partners.
Learn more about the importance of supply chain partners following email security best practices.
Along with being used to gain visibility and control over your domains and protect them from exploits, dmarcian’s DMARC Management Platform and free tools are resources for auditing and monitoring your supply chain as a part of your vendor management strategy.

How dmarcian can help
With a team of email security experts and a mission of making email and the internet more trustworthy through domain security, dmarcian is here to help assess an organization’s domain catalog and implement and manage DMARC for the long haul. You can register for a free trial, where our onboarding and support team will help you along the way.
Want to continue the conversation? Head over to the dmarcian Forum.


