
Out of the Wilderness: Upgrading the Email Security Model
Email has long been recognized as the #1 vector for online attacks. Despite decades of investment in developing defenses to protect people and organizations from email-borne fraud, the situation keeps getting worse. The Traditional Email Security Model is rooted in concepts of perimeter defense, leading to systemic flaws that no amount of investment can overcome.
An upgraded email security model is now available that corrects the fundamental flaws of the traditional model—the DMARC-based Email Security Model. Organizations can opt into this model by deploying DMARC and configuring existing email processing systems to implement the upgraded email security model.
Table of contents
- Email is the #1 Attack Vector
- The Effectiveness of Phishing
- The Traditional Email Security Model
- Email Shows Its Age
- Spam Filters
- When Filtering Doesn’t Work
- Spam Folders: Visible Symptom
- More Spam Folder: Legit vs. Fraudulent
- Why Phishing Leads Attacks
- DMARC-based Email Security Model
- Protecting People from Dangerous Decisions
- Filter in What Is Wanted
- Zero Trust Meets Email
- Permitted Domains
- Conclusion
Email is the #1 Attack Vector
Email is so heavily embedded into the threat landscape that finding simple statistics on it is becoming increasingly difficult. Optery has taken up the mantle and analyzed the 2025 Verizon Data Breach Report to show that behind the categories of Incident Classification Patterns, email remains “the most consequential vector in the threat landscape.”
Couched in terms of losses, data from the FBI’s Public Service Announcement from 11 September 2024 (I-091124-PSA) notes that losses from Business Email Compromise (BEC) between October 2013 and December 2023 amount to $55.5 billion.
Though it’s focused on the United States, FBI data is important as it describes a well-defined and narrow category of email-enabled fraud—that of BEC. According to the FBI, BEC “is a sophisticated scam that targets both businesses and individuals who perform legitimate transfer-of-funds requests.” Considering this narrow band of email-enabled fraud, $55.5 billion is a staggering loss.
To give a taste of how these losses continue—and are increasing—data from the 2024 FBI Internet Crime Report indicates more than $16 billion in overall internet crime losses, noting a 33% increase in losses from 2023.
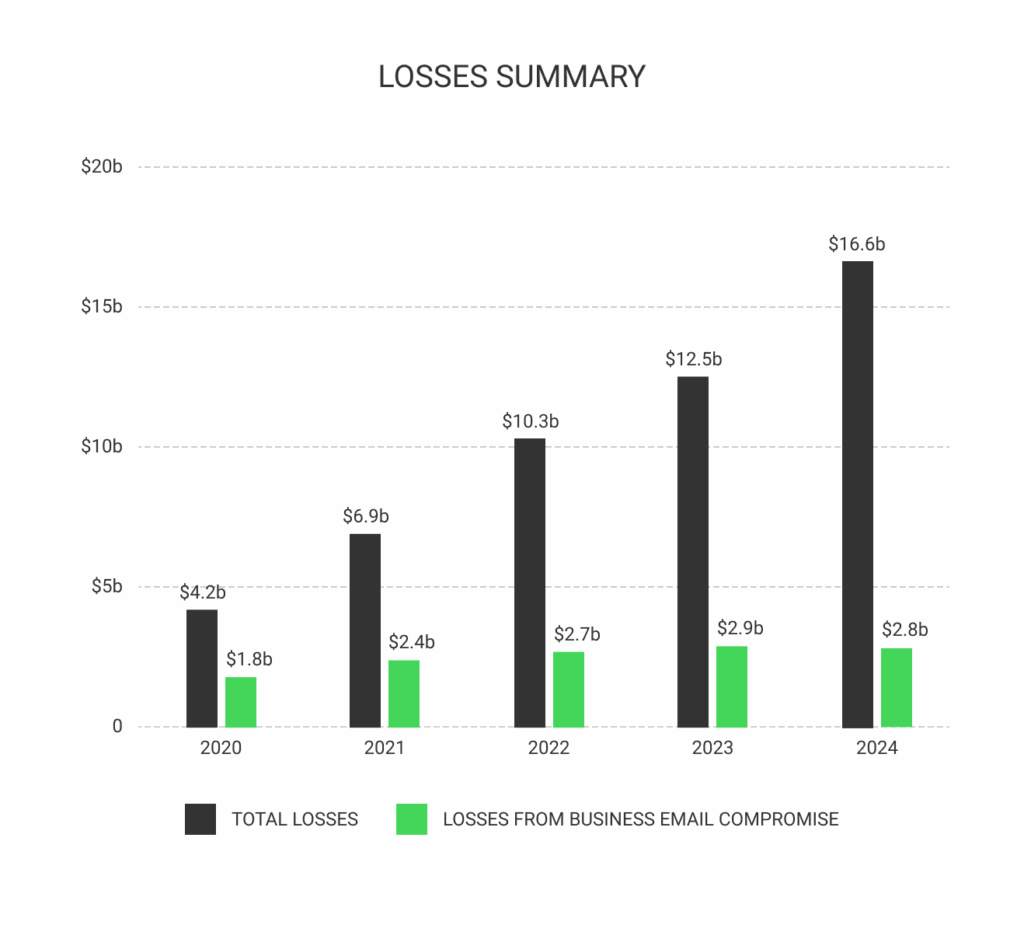
$2.8 billion of the $16 billion are losses due to the narrow band of email-enabled BEC fraud. Actual losses because of email-enabled crime cannot be calculated, but the FBI-reported slice of crime is enough to recognize the magnitude of the problem.
The Effectiveness of Phishing
Deceptive email tries to impersonate a trusted entity in order to trick a person into revealing protected information or granting otherwise unauthorized access. This type of email is colloquially known as phishing.
Phishing is effective for three simple reasons:
- Email is used everywhere, by everyone, all the time.
- No one owns email. Email is not a product provided by a single company. Email is the result of many separate systems all interoperating in different ways to provide a global service.
- Email predates the World Wide Web, is arguably the largest installed application on the internet, and comes from a time before modern security was invented.
With email’s universal presence, it inadvertently finds itself leveraged as the tool of first choice when attackers are looking to break into an organization.
The Traditional Email Security Model
An increasingly hostile email environment led to the evolution of ad hoc defensive technologies, largely based around an organization’s ability to buy a product or service to protect its own users from fraud.
The following sections briefly describe how and why those technologies came to be and the resulting arms race that has upped the stakes for everyone without meeting the promise of security.
Email Shows Its Age
Email predates modern internet security. The first email messages were sent in the 1970s, where the focus was on making email work when computers were first being connected.
A couple of decades would pass before Internet security as we know it came about. As such, by default email does not include security mechanisms to protect itself from modern fraud.
Today’s email consists of many thousands of different systems that work together by adhering to internet interoperability standards like RFC 5598. Those standards allow anyone to implement their own piece or component of the email system. This also means that any change in how email interoperates takes many years to gain traction, if any traction is gained at all. There is no way to get everyone to update so much software all at the same time.
Spam Filters
Rather than change how email works, the Traditional Email Security Model came into existence where most organizations have control—at the border into their own organization. Traditionally, organizations have had to filter out unwanted email, be it phishing, malware, spam, or other nuisance email. Security companies invented technology and sold products to filter out substantial amounts of unwanted email. Today, these technologies are collectively referred to as “spam filters.”
When Filtering Doesn’t Work
Fundamentally, the security model of “filter out unwanted email” contains a flaw. Despite blocking substantial amounts of unwanted email, the best filtering technology still breaks down in two distinct ways:
- When pattern-detecting machines have to deal with an unknown pattern, and
- when fraudulent emails look too similar to legitimate emails for machines to make a definitive decision regarding the legitimacy of an email.
These two different failure points are two sides of the same flawed coin—that of machines being forced to guess as to the authenticity of any single piece of email.
Spam Folders: Visible Symptom
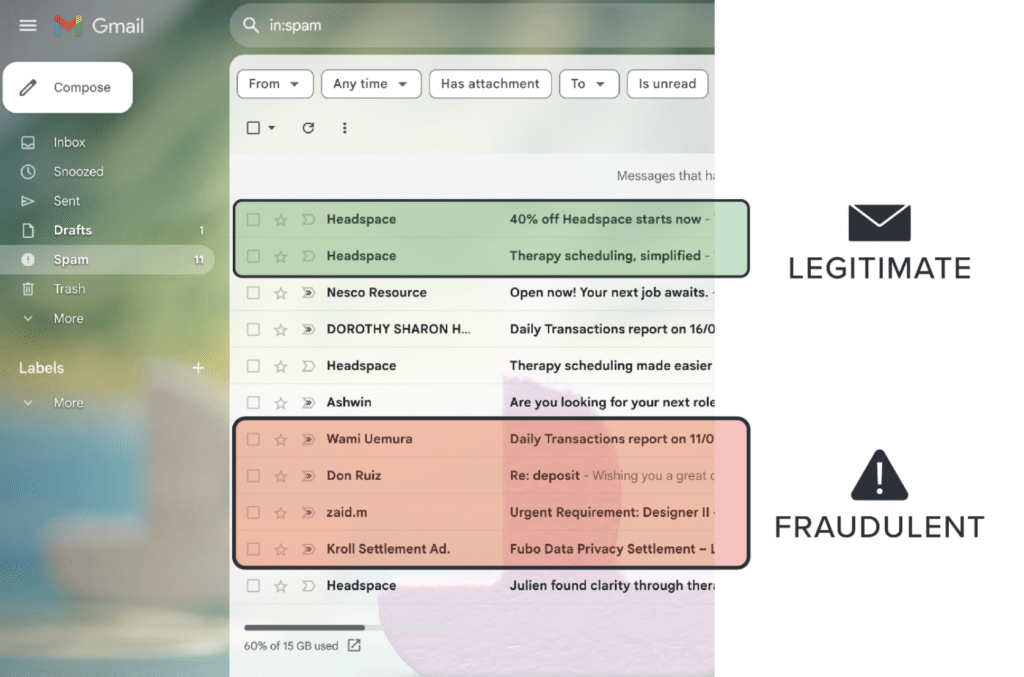
The most visible symptom of the flaw is the ubiquitous “spam folder.” When machines cannot tell between fraudulent email that looks legitimate and legitimate email that has a whiff of fraudulence, the machines place such email into a spam folder.
A company that supplies spam filters cannot afford to accidentally block legitimate email, and the workaround is to place difficult-to-classify email into a spam folder or quarantine for human evaluation.
To make this scenario worse, bad actors treat this situation like a game where solving the puzzle of getting harmful email through filters can lead to big payoffs. Tools like AI are now making it far easier for bad actors to both play and win.
More Spam Folder: Legit vs. Fraudulent
The result of this traditional security model is that real people largely do not have to deal with a large amount of unwanted email. However, the resulting malicious email that gets through ends up in an inbox or a spam folder where real humans have to figure out if what they’re looking at is legitimate-and-poorly-worded or extremely dangerous.
Due to the numbers involved, even if 1 out of 100,000 malicious emails end up in a spam folder, chances are a real human will be deceived by an email that managed to get through cutting-edge filtering technology, or what was considered cutting-edge when the technology was originally procured.
Why Phishing Leads Attacks
The net is that email remains the #1 attack vector, despite decades of investment in the Traditional Email Security Model’s assumption that if bad stuff can be filtered out, what remains can be assumed to be good.
DMARC-based Email Security Model
To correct this fundamental flaw of assumption, the DMARC Email Security Model implements Zero Trust Architectural concepts within the world of email communications. DMARC is an internet standard that describes how to attach a reliable reference to the internet domain that authored an email.
DMARC builds upon the existing email authentication technologies of SPF and DKIM to create a link between a domain and an email. The technical aspects of DMARC, SPF, and DKIM are discussed in other articles.
Protecting People from Dangerous Decisions
Putting the most dangerous emails in front of normal humans to decide whether or not they’re dangerous isn’t a good model.
Filter in What Is Wanted
Instead of assuming that all email is legitimate and then attempting to filter out unwanted email, the DMARC Security Model requires email to be legitimized by authenticating back to the email’s sending internet domain. In this way, the DMARC Security Model “filters in” legitimate email as opposed to the traditional way of assuming email is legitimate and attempting to filter out what can be detected as malicious.

Zero Trust Meets Email
To flip the Traditional Email Security Model on its head, DMARC introduces a foundation of stable, domain-level identifiers that are associated with email. These identifiers provide the basis for Zero Trust Architectures within email. Zero Trust Architectures explicitly assume trust is absent until proven otherwise. DMARC’s domain-level identifiers provide the foundation for trust to be established while processing email.
Stable, domain-level identifiers allow email operators to build protections at the machine level so that people do not need to be confronted with spam folders full of extremely dangerous email mixed in with spammy-looking legitimate email. In our retail resource example above, domains are associated with waiting people. Security then inspects the domain when deciding to grant access.
Permitted Domains
When the DMARC Security Model is adopted, organizations that send DMARC-compliant email can immediately put in place controls to protect personnel from bad actors that pretend to be fellow colleagues. As vendors and supply chains send DMARC-compliant email, organizations can add further controls to create protected channels of email communications that takes human guesswork out of determining legitimacy.
In our example, legitimate and trustworthy domains like dmarcian.com are accepted, whereas unwanted domains that are intended to trick people like the misspelled gmale.com and hotmale.com are refused.
Conclusion
This article provides context regarding the traditional state of email security, where it fails and how the DMARC-based email security model brings Zero Trust Architectural concepts to the world of email.
A video version of this article was produced for the Payment Card Industry’s content library.
Want to continue the conversation? Head over to the dmarcian Forum.


